Adversaries Love Single Layered EDR, but They Will Hate Infopercept's Defense-in-Depth Protection
On April 15, 2022
Adversaries and cybersecurity have been playing the cat and mouse game for years now. Every time we think a particular advancement in a cybersecurity solution or method will be enough to prevent adversaries, we are shocked by a new cyberattack. Adversaries always find a way to circumvent cybersecurity solutions.
Earlier anti-virus was enough and now Endpoint Detection and Response with Artificial Intelligence and Machine Learning is considered to be enough. However, considering the number of ransomware attacks, and the increasing number in breaches and vulnerabilities; it appears that the adversaries have found a way around Endpoint Detection and Response solutions.
In fact, it seems that the adversaries must be loving EDRs as they have become so easy to exploit or bypass. Taking this as a challenge and working on Gartner’s recommendation of adopting Defense-in-Depth, Infopercept has launched a five-layered Defence-In-Depth single installation. This End Point Security not only provides a layered security but also doesn’t hinder performance.
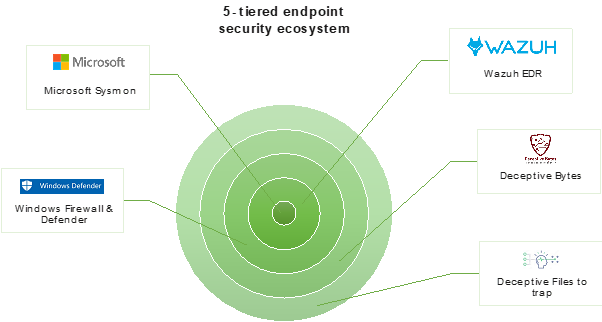
Infopercept’s Defense-In-Depth Single Installer and Monitoring is the newest major release which is designed with Gartner Defense-In-Depth recommendation:
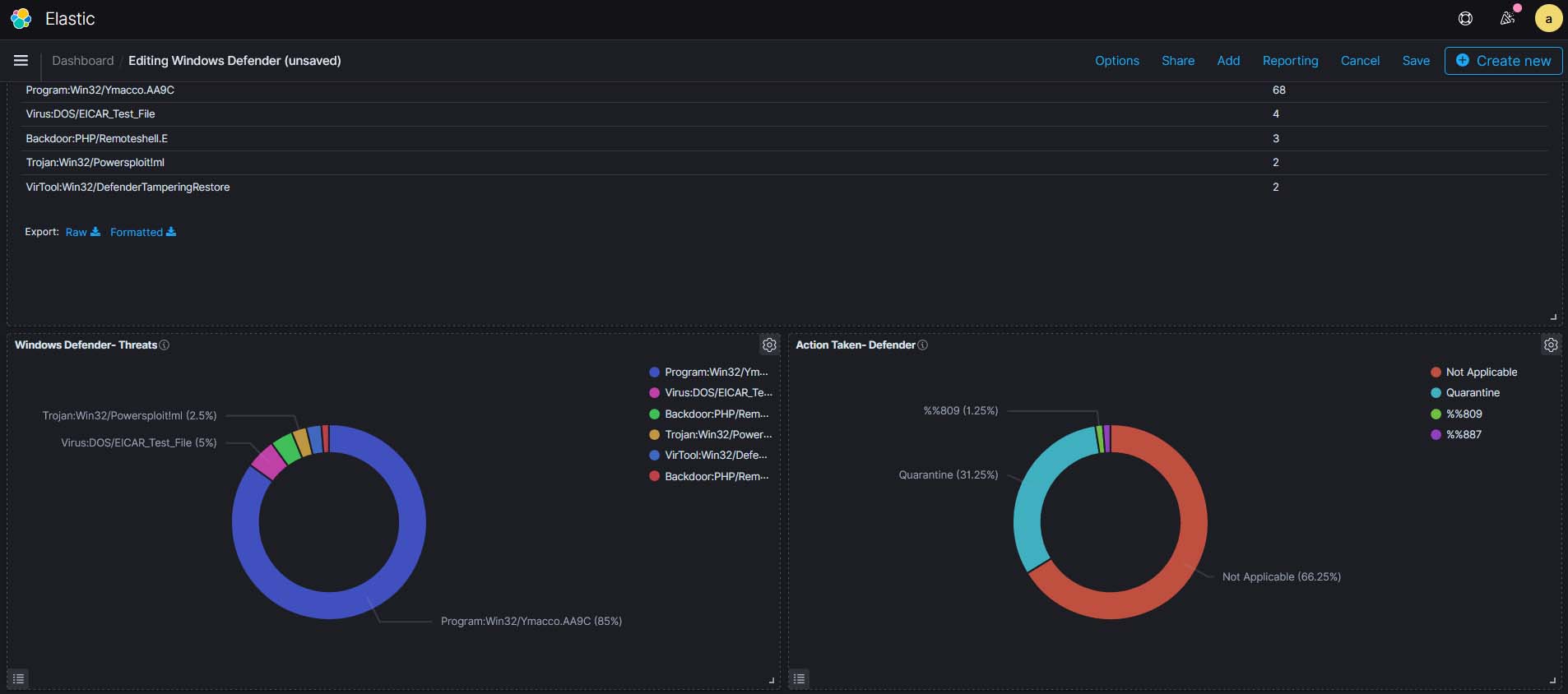
1.Focusing on the known attacks with the Gartner Leading Anti-Virus. Windows Defender is better than most antiviruses, especially with the addition of sandboxing tools and cloud-based malware detection - features that aren’t included with many free antivirus programs. (Most important there is no additional license cost)
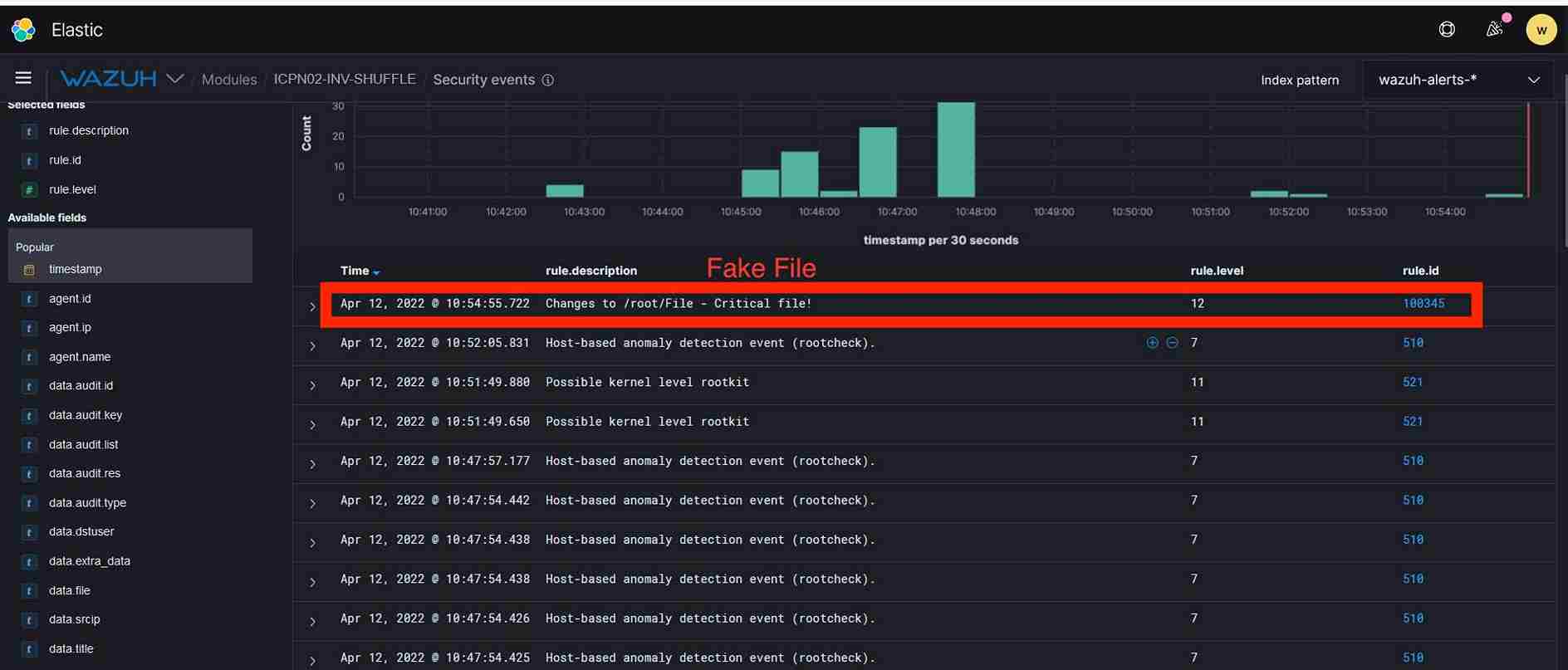
2.Prevent unknown attacks with Deceptive Bytes (End Point Deception). The solution creates dynamic & deceptive information which interferes with any attempt to recon the environment and deters the malware from executing its malicious intents, through all the stages of compromise in the Attack Kill Chain - covering advanced & sophisticated malware techniques, constantly making sure all the endpoints & data in the enterprise are secured. (The solution has no impact on performance and does not require updates of signature as this is signature less innovation)
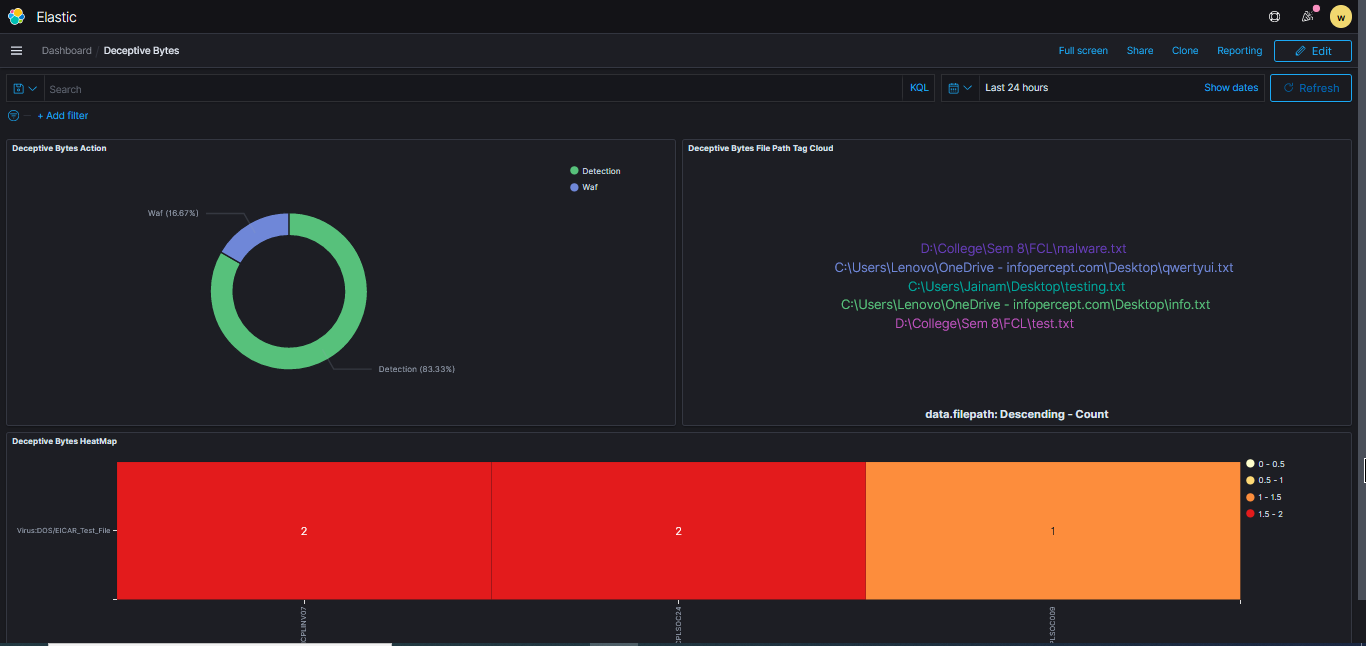
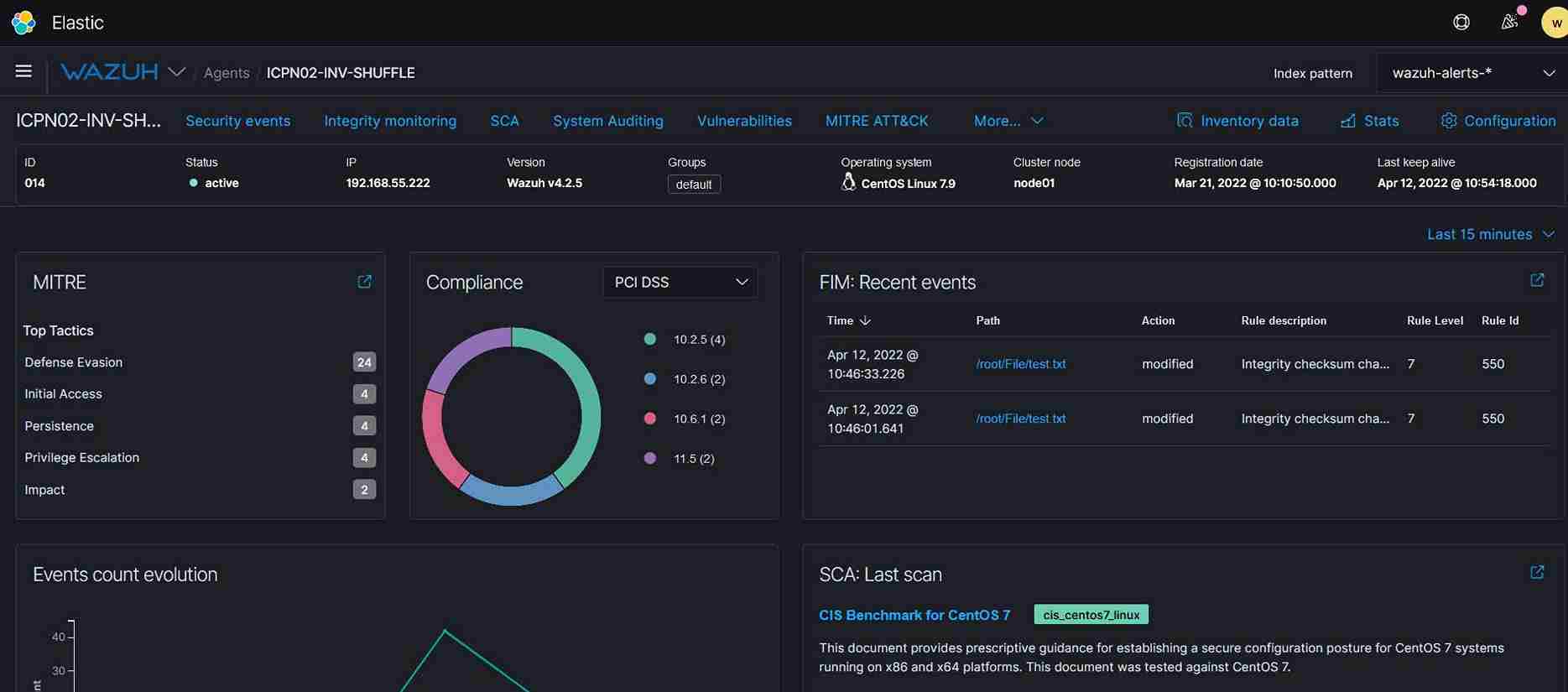
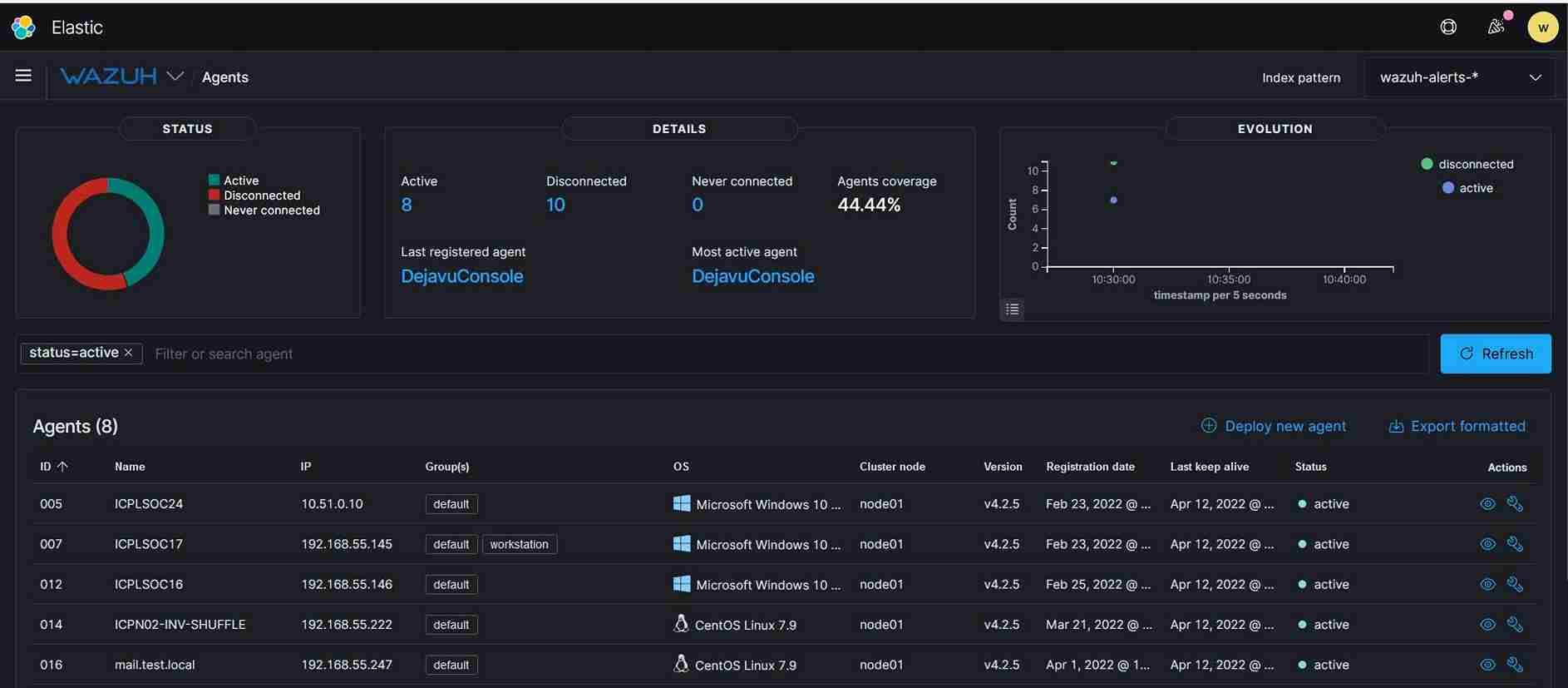
3.Detection and Response (EDR - End Point Detection and Response) which addresses - Log and events data collection, File and registry keys integrity monitoring, Inventory of running processes and installed applications, Monitoring of open ports and network configuration, Detection of rootkits or malware artifacts, Configuration assessment and policy monitoring, and Execution of active responses.
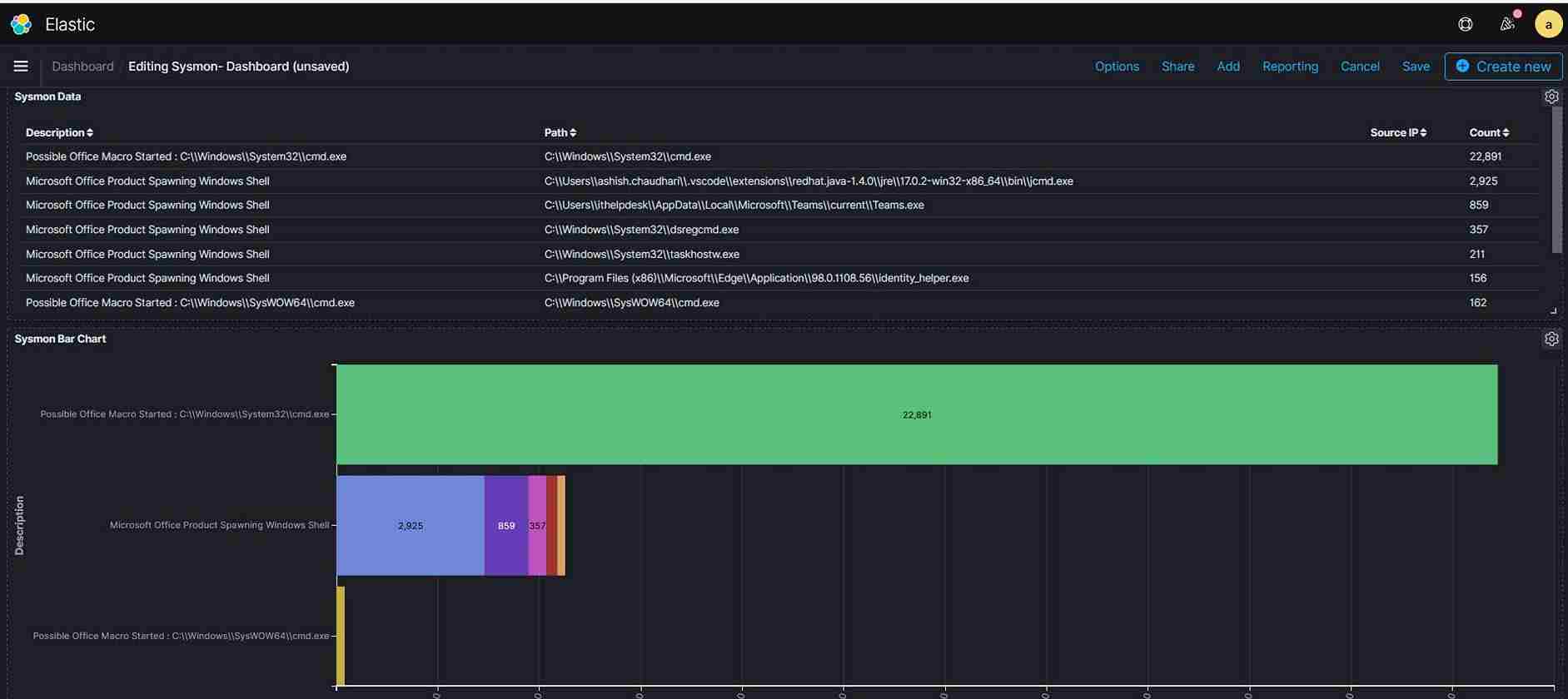
4.Increase visibility in depth and breadth - T System Monitor (Sysmon) is a Windows system service and device driver that, once installed on a system, remains resident across system reboots to monitor and log system activity to the Windows event log. It provides detailed information about process creations, network connections, and changes to file creation time which is critical for analysing security. (The advantage is a no cost and performance impact of using this service)
5.Placing the Fake File and Fake Username & Passwords to attract and defend - Placement of Fake Files and Fake Password will be a unique strategy to attract attackers in their own game.