Additional AWS EventNames
On April 15, 2022
On Monday, October 4, 2021, Apache published an advisory on CVE-2021-41773, Amazon CloudTrail is an excellent data source with a lot of API call history that allows us to keep track of who is attempting to do what in our AWS accounts.
But there is a little bit of problem with that too. We have a lot of call logging to analyze because every call is logged (including role assumption, role switching, and even the creation of a log stream).
According to a study, out of 400 million Cloud Trail Events, users just want only1 in 25,000 to be alerted of CloudTrail events. That’s an incredible signal-to-noise ratio!
Wazuh has a CDB List of AWS EventNames to reduce the signal-to-noise ratio and get the appropriate logs which needs to be monitored.
What is a CDB List?
A CDB List (Constant Database) is a collection of values that are compared to a field extracted by a decoder. A custom rule checks whether the IP, user, or any other extracted information is present in the list from which we can determine whether or not to generate an alert based on the outcome.
How does it works with Wazuh?
Wazuh is a free, open source, enterprise-ready security monitoring technology that detects threats, monitors integrity, responds to incidents, and ensures compliance.
This feature’s primary purpose is to create a white/black list of users, file hashes, IP addresses, and domain names.
The list file is a simple text file with the following format for each line:
key1:value1
key2:value2
Each key must be unique, be preceded by a colon, and can contain an optional value. The value can be the others, but the key must be unique.
We can determine the existence or absence of a field in a list using a key. We can utilize a value as some rule criteria by adding it. For example, if we have account names (keys) that are linked to department names (values), we may create an alert that is triggered when a user who is not from the finance department connects into the finance server.
Adding Additonal AWS EventNames in the CDB List
Wazuh has a default CDB list for AWS EventNames located in /var/ossec/etc/lists/amazon/aws-EventNames consisting of 346 EventNames by default.
There are some more AWS EventNames to be added of which logs are needed to be monitored:
AttachLoadBalancers:Autoscaling
DetachLoadBalancers:Autoscaling
PutScalingPolicy:Autoscaling
TerminateInstanceInAutoScalingGroup:Autoscaling
CancelUpdateStack:Cloudformation
CreateStack:Cloudformation
DeleteStack:Cloudformation
UpdateStack:Cloudformation
DeleteConfigRule:AWS Config
DeleteConfigurationRecorder:AWS Config
DeleteDeliveryChannel:AWS Config
DeleteEvaluationResults:AWS Config
PutConfigurationRecorder:AWS Config
PutConfigRule:AWS Config
PutDeliveryChannel:AWS Config
PutEvaluations:AWS Config
StartConfigRulesEvaluation:AWS Config
StartConfigurationRecorder:AWS Config
StopConfigurationRecorder:AWS Config
RunInstances:EC2
StartInstances:EC2
StopInstances:EC2
TerminateInstances:EC2
UpdateInstanceInformation:EC2
DescribeAddresses:EC2
DescribeKeyPairs:EC2
DescribeNetworkAcls:EC2
DescribeSecurityGroups:EC2
DescribeVpcs:EC2
AbortEnvironmentUpdate:Elastic Beanstalk
CreateApplication:Elastic Beanstalk
CreateApplicationVersion:Elastic Beanstalk
CreateConfigurationTemplate:Elastic Beanstalk
CreateEnvironment:Elastic Beanstalk
CreateStorageLocation:Elastic Beanstalk
DeleteApplication:Elastic Beanstalk
DeleteStack:Cloudformation
UpdateStack:Cloudformation
DeleteConfigRule:AWS Config
DeleteConfigurationRecorder:AWS Config
DeleteDeliveryChannel:AWS Config
DeleteEvaluationResults:AWS Config
PutConfigurationRecorder:AWS Config
PutConfigRule:AWS Config
PutDeliveryChannel:AWS Config
PutEvaluations:AWS Config
StartConfigRulesEvaluation:AWS Config
StartConfigurationRecorder:AWS Config
StopConfigurationRecorder:AWS Config
RunInstances:EC2
StartInstances:EC2
StopInstances:EC2
TerminateInstances:EC2
UpdateInstanceInformation:EC2
DescribeAddresses:EC2
DescribeKeyPairs:EC2
DescribeNetworkAcls:EC2
DescribeSecurityGroups:EC2
DescribeVpcs:EC2
AbortEnvironmentUpdate:Elastic Beanstalk
CreateApplication:Elastic Beanstalk
CreateApplicationVersion:Elastic Beanstalk
CreateConfigurationTemplate:Elastic Beanstalk
CreateEnvironment:Elastic Beanstalk
CreateStorageLocation:Elastic Beanstalk
DeleteApplication:Elastic Beanstalk
DeleteApplicationVersion:Elastic Beanstalk
DeleteConfigurationTemplate:Elastic Beanstalk
DeleteEnvironmentConfiguration:Elastic Beanstalk
RebuildEnvironment:Elastic Beanstalk
RestartAppServer:Elastic Beanstalk
SwapEnvironmentCNAMEs:Elastic Beanstalk
TerminateEnvironment:Elastic Beanstalk
UpdateApplication:Elastic Beanstalk
UpdateApplicationVersion:Elastic Beanstalk
UpdateConfigurationTemplate:Elastic Beanstalk
UpdateEnvironment:Elastic Beanstalk
CreateFileSystem:EFS
CreateMountTarget:EFS
DeleteFileSystem:EFS
DeleteMountTarget:EFS
CreateListener:ELB
CreateLoadBalancer:ELB
CreateLoadBalancerListeners:ELB
CreateLoadBalancerPolicy:ELB
CreateTargetGroup:ELB
DeleteListener:ELB
DeleteLoadBalancer:ELB
DeleteLoadBalancerListeners:ELB
DeleteLoadBalancerPolicy:ELB
DeleteTargetGroup:ELB
DeregisterInstancesFromLoadBalancer:ELB
DeregisterTargets:ELB
DetachLoadBalancerFromSubnets:ELB
DisableAvailabilityZonesForLoadBalancer:ELB
EnableAvailabilityZonesForLoadBalance:ELB
ModifyListener:ELB
ModifyLoadBalancerAttributes:ELB
ModifyRule:ELB
ModifyTargetGroup:ELB
ModifyTargetGroupAttributes:ELB
RegisterInstancesWithLoadBalancer:ELB
RegisterTargets:ELB
RemoveTags:ELB
CreateDBCluster:RDS
CreateDBClusterParameterGroup:RDS
CreateDBClusterSnapshot:RDS
CreateDBInstance:RDS
CreateDBInstanceReadReplica:RDS
CreateDBParameterGroup:RDS
CreateDBSnapshot:RDS
CreateDBSubnetGroup:RDS
CreateOptionGroup:RDS
DeleteDBCluster:RDS
DeleteDBClusterParameterGroup:RDS
DeleteDBClusterSnapshot:RDS
DeleteDBInstance:RDS
DeleteDBParameterGroup:RDS
DeleteDBSnapshot:RDS
DeleteDBSubnetGroup:RDS
DeleteOptionGroup:RDS
FailoverDBCluster:RDS
ModifyDBCluster:RDS
ModifyDBClusterParameterGroup:RDS
ModifyDBInstance:RDS
ModifyDBParameterGroup:RDS
ModifyDBSnapshotAttribute:RDS
ModifyDBSubnetGroup:RDS
ModifyOptionGroup:RDS
PromoteReadReplica:RDS
RebootDBInstance:RDS
ResetDBClusterParameterGroup:RDS
ResetDBParameterGroup:RDS
RestoreDBClusterFromSnapshot:RDS
RestoreDBClusterToPointInTime:RDS
RestoreDBInstanceFromDBSnapshot:RDS
RestoreDBInstanceToPointInTime:RDS
ChangeResourceRecordSets:Route53
DeleteHealthCheck:Route53
CreateBucket:S3
DeleteBucket:S3
DeleteBucketLifecycle:S3
DeleteBucketReplication:S3
DeleteBucketTagging:S3
PutBucketLifecycle:S3
PutBucketLogging:S3
PutBucketNotification:S3
PutBucketReplication:S3
PutBucketRequestPayment:S3
PutBucketTagging:S3
PutBucketVersioning:S3
GetBucketLogging:S3
GetBucketPolicy:S3
GetBucketPolicyStatus:S3
ConsoleLogin:Access
ExitRole:Access
RenewRole:Access
SwitchRole:Access
DeleteCertificate:Certificate Manager
RequestCertificate:Certificate Manager
ResendValidationEmail:Certificate Manager
StopLogging:Cloudtrail
AllocateConnectionOnInterconnect:Direct Connect
AllocateHostedConnection:Direct Connect
AllocatePrivateVirtualInterface:Direct Connect
AllocatePublicVirtualInterface:Direct Connect
AssociateConnectionWithLag:Direct Connect
AssociateHostedConnection:Direct Connect
AssociateVirtualInterface:Direct Connect
ConfirmConnection:Direct Connect
ConfirmPrivateVirtualInterface:Direct Connect
ConfirmPublicVirtualInterface:Direct Connect
CreateConnection:Direct Connect
CreateInterconnect:Direct Connect
CreateLag:Direct Connect
CreatePrivateVirtualInterface:Direct Connect
CreatePublicVirtualInterface:Direct Connect
DeleteConnection:Direct Connect
DeleteInterconnect:Direct Connect
DeleteLag:Direct Connect
DeleteVirtualInterface:Direct Connect
DisassociateConnectionFromLag:Direct Connect
UpdateLag:Direct Connect
AssociateIamInstanceProfile:EC2 - VPC
AssociateAddress:EC2 - VPC
AssociateRouteTable:EC2 - VPC
AssociateSubnetCidrBlock:EC2 - VPC
AssociateVpcCidrBlock:EC2 - VPC
AttachClassicLinkVpc:EC2 - VPC
AttachInternetGateway:EC2 - VPC
AttachNetworkInterface:EC2 - VPC
AllocateAddress:EC2 - VPC
AssignPrivateIpAddresses:EC2 - VPC
AttachVpnGateway:EC2 - VPC
CreateKeyPair:EC2 - VPC
CreateNatGateway:EC2 - VPC
CreateNetworkAcl:EC2 - VPC
CreateNetworkAclEntry:EC2 - VPC
CreateNetworkInterface:EC2 - VPC
CreateRoute:EC2 - VPC
CreateRouteTable:EC2 - VPC
CreateSecurityGroup:EC2 - VPC
CreateVpc:EC2 - VPC
CreateVpcEndpoint:EC2 - VPC
CreateVpcPeeringConnection:EC2 - VPC
CreateVpnConnection:EC2 - VPC
CreateVpnConnectionRoute:EC2 - VPC
CreateVpnGateway:EC2 - VPC
DeleteCustomerGateway:EC2 - VPC
DeleteDhcpOptions:EC2 - VPC
DeleteEgressOnlyInternetGateway:EC2 - VPC
DeleteInternetGateway:EC2 - VPC
DeleteKeyPair:EC2 - VPC
DeleteNatGateway:EC2 - VPC
DeleteNetworkAcl:EC2 - VPC
DeleteNetworkAclEntry:EC2 - VPC
DeleteNetworkInterface:EC2 - VPC
DeleteRoute:EC2 - VPC
DeleteRouteTable:EC2 - VPC
DeleteSecurityGroup:EC2 - VPC
DeleteVpcEndpoints:EC2 - VPC
DeleteVpcPeeringConnection:EC2 - VPC
DeleteVpnConnection:EC2 - VPC
DeleteVpnConnectionRoute:EC2 - VPC
DeleteVpnGateway:EC2 - VPC
DetachClassicLinkVpc:EC2 - VPC
DetachInternetGateway:EC2 - VPC
DetachNetworkInterface:EC2 - VPC
DetachVolume:EC2 - VPC
DetachVpnGateway:EC2 - VPC
DisableVgwRoutePropagation:EC2 - VPC
DisableVpcClassicLink:EC2 - VPC
DisassociateAddress:EC2 - VPC
DisassociateIamInstanceProfile:EC2 - VPC
DisassociateRouteTable:EC2 - VPC
DisassociateSubnetCidrBlock:EC2 - VPC
DisassociateVpcCidrBlock:EC2 - VPC
EnableVgwRoutePropagation:EC2 - VPC
EnableVolumeIO:EC2 - VPC
EnableVpcClassicLink:EC2 - VPC
AuthorizeSecurityGroupEgress:EC2 - Security Groups
AuthorizeSecurityGroupIngress:EC2 - Security Groups
RevokeSecurityGroupEgress:EC2 - Security Groups
RevokeSecurityGroupIngress:EC2 - Security Groups
ModifyMountTargetSecurityGroups:EFS
ApplySecurityGroupsToLoadBalancer:ELB
SetSecurityGroups:ELB
AuthorizeCacheSecurityGroupIngress:ElastiCache
CreateCacheSecurityGroup:ElastiCache
DeleteCacheSecurityGroup:ElastiCache
RevokeCacheSecurityGroupIngress:ElastiCache
AddClientIDToOpenIDConnectProvider:IAM
AddRoleToInstanceProfile:IAM
AddUserToGroup:IAM
AttachGroupPolicy:IAM
AttachRolePolicy:IAM
AttachUserPolicy:IAM
ChangePassword:IAM
CreateAccessKey:IAM
CreateAccountAlias:IAM
CreateGroup:IAM
CreateInstanceProfile:IAM
CreateLoginProfile:IAM
CreateOpenIDConnectProvider:IAM
CreatePolicy:IAM
CreatePolicyVersion:IAM
CreateRole:IAM
CreateSAMLProvider:IAM
CreateUser:IAM
CreateVirtualMFADevice:IAM
DeactivateMFADevice:IAM
DeleteAccessKey:IAM
DeleteAccountAlias:IAM
DeleteAccountPasswordPolicy:IAM
DeleteGroup:IAM
DeleteGroupPolicy:IAM
DeleteInstanceProfile:IAM
DeleteLoginProfile:IAM
DeleteOpenIDConnectProvider:IAM
DeletePolicy:IAM
DeletePolicyVersion:IAM
DeleteRole:IAM
DeleteRolePolicy:IAM
DeleteSAMLProvider:IAM
DeleteServerCertificate:IAM
DeleteSigningCertificate:IAM
DeleteSSHPublicKey:IAM
DeleteUser:IAM
DeleteUserPolicy:IAM
DeleteVirtualMFADevice:IAM
DetachGroupPolicy:IAM
DetachRolePolicy:IAM
DetachUserPolicy:IAM
EnableMFADevice:IAM
PutGroupPolicy:IAM
PutRolePolicy:IAM
PutUserPolicy:IAM
RemoveClientIDFromOpenIDConnectProvider:IAM
RemoveRoleFromInstanceProfile:IAM
RemoveUserFromGroup:IAM
ResyncMFADevice:IAM
SetDefaultPolicyVersion:IAM
UpdateAccessKey:IAM
ListAccessKey:IAM
ListSSHPublicKeys:IAM
UpdateAccountPasswordPolicy:IAM
UpdateAssumeRolePolicy:IAM
UpdateGroup:IAM
UpdateLoginProfile:IAM
UpdateOpenIDConnectProviderThumbprint:IAM
UpdateSAMLProvider:IAM
UpdateServerCertificate:IAM
UpdateSigningCertificate:IAM
UpdateSSHPublicKey:IAM
UpdateUser:IAM
UploadServerCertificate:IAM
UploadSigningCertificate:IAM
UploadSSHPublicKey:IAM
GetInstanceProfile:IAM
GetUser:IAM
ListUserPolicies:IAM
ListUserTags:IAM
AssumeRole:STS
AuthorizeSnapshotAccess:Redshift
RevokeSnapshotAccess:Redshift
RotateEncryptionKey:Redshift
AuthorizeClusterSecurityGroupIngress:Redshift
CreateClusterSecurityGroup:Redshift
DeleteClusterSecurityGroup:Redshift
RevokeClusterSecurityGroupIngress:Redshift
AuthorizeDBSecurityGroupIngress:RDS
CreateDBSecurityGroup:RDS
DeleteDBSecurityGroup:RDS
RevokeDBSecurityGroupIngress:RDS
DeleteBucketCors:S3
DeleteBucketPolicy:S3
DeleteBucketWebsite:S3
PutBucketAcl:S3
PutBucketCors:S3
PutBucketPolicy:S3
PutBucketWebsite:S3
RestoreObject:S3
ReplicateTags:S3
ReplicateObject:S3
ReplicateDelete:S3
PutObjectVersionTagging:S3
PutObjectVersionAcl:S3
PutObjectTagging:S3
PutObjectRetention:S3
PutObjectLegalHold:S3
PutObjectAcl:S3
PutObject:S3
ListObjects:S3
ListMultipartUploadParts:S3
ListBucketMultipartUploads:S3
ListBucketVersions:S3
ListBucket:S3
GetObjectVersionTagging:S3
GetObjectVersionAcl:S3
GetObjectVersion:S3
GetObjectTagging:S3
GetObjectRetention:S3
GetObjectAcl:S3
GetObject:S3
DeleteObjectVersionTagging:S3
DeleteObjectVersion:S3
DeleteObjectTagging:S3
DeleteObject:S3
DeleteObjects:S3
ObjectCreated:S3
GetBucketReplication:S3
GetBucketRequestPayment:S3
ListTables:DynamoDB
ListBackups:DynamoDB
DescribeTableStatistics:DynamoDB
DescribeTableSettings:DynamoDB
DescribeKinesisStreamingDestination:DynamoDB
CreateByteMatchSet:WAF
CreateIPSet:WAF
CreateRule:WAF
CreateSizeConstraintSet:WAF
CreateSqlInjectionMatchSet:WAF
CreateWebACL:WAF
CreateXssMatchSet:WAF
DeleteByteMatchSet:WAF
DeleteIPSet:WAF
DeleteRule:WAF
DeleteSizeConstraintSet:WAF
DeleteSqlInjectionMatchSet:WAF
DeleteWebACL:WAF
DeleteXssMatchSet:WAF
UpdateByteMatchSet:WAF
UpdateIPSet:WAF
UpdateRule:WAF
UpdateSizeConstraintSet:WAF
UpdateSqlInjectionMatchSet:WAF
UpdateWebACL:WAF
UpdateXssMatchSet:WAF
AssociateDhcpOptions:Legacy Wazuh CDB
AttachVolume:Legacy Wazuh CDB
CopySnapshot:Legacy Wazuh CDB
CreateImage:Legacy Wazuh CDB
CreatePlacementGroup:Legacy Wazuh CDB
CreateSnapshot:Legacy Wazuh CDB
CreateSubnet:Legacy Wazuh CDB
CreateTags:Legacy Wazuh CDB
CreateVolume:Legacy Wazuh CDB
DeletePlacementGroup:Legacy Wazuh CDB
DeleteSnapshot:Legacy Wazuh CDB
DeleteTags:Legacy Wazuh CDB
DeleteVolume:Legacy Wazuh CDB
DeregisterImage:Legacy Wazuh CDB
DisableKey:Legacy Wazuh CDB
GetGroup:Legacy Wazuh CDB
ListAliases:Legacy Wazuh CDB
ListGroups:Legacy Wazuh CDB
ListUsers:Legacy Wazuh CDB
ModifyImageAttribute:Legacy Wazuh CDB
ModifyInstanceAttribute:Legacy Wazuh CDB
ModifyNetworkInterfaceAttribute:Legacy Wazuh CDB
ModifySnapshotAttribute:Legacy Wazuh CDB
ModifySubnetAttribute:Legacy Wazuh CDB
ModifyVolumeAttribute:Legacy Wazuh CDB
MonitorInstances:Legacy Wazuh CDB
RebootInstances:Legacy Wazuh CDB
RegisterImage:Legacy Wazuh CDB
UnmonitorInstances:Legacy Wazuh CDB
UpdateInstanceAlias:Legacy Wazuh CDB
AddMemberToGroup:SSO
CompleteVirtualMfaDeviceRegistration:SSO
CompleteWebAuthnDeviceRegistration:SSO
CreateAlias:SSO
CreateExternalIdPConfigurationForDirectory:SSO
CreateGroup:SSO
CreateUser:SSO
DeleteExternalIdPConfigurationForDirectory:SSO
DeleteGroup:SSO
DeleteMfaDeviceForUser:SSO
DeleteUser:SSO
DescribeDirectory:SSO
DescribeGroups:SSO
DescribeUsers:SSO
DisableExternalIdPConfigurationForDirectory:SSO
DisableUser:SSO
EnableExternalIdPConfigurationForDirectory:SSO
EnableUser:SSO
GetAWSSPConfigurationForDirectory:SSO
ListExternalIdPConfigurationsForDirectory:SSO
ListGroupsForUser:SSO
ListMembersInGroup:SSO
ListMfaDevicesForUser:SSO
PutMfaDeviceManagementForDirectory:SSO
RemoveMemberFromGroup:SSO
SearchGroups:SSO
SearchUsers:SSO
StartVirtualMfaDeviceRegistration:SSO
StartWebAuthnDeviceRegistration:SSO
UpdateExternalIdPConfigurationForDirectory:SSO
UpdateGroup:SSO
UpdateMfaDeviceForUser:SSO
UpdatePassword:SSO
UpdateUser:SSO
VerifyEmail:SSO
CreateToken:SSO
RegisterClient:SSO
StartDeviceAuthorization:SSO
Authenticate:SSO
Federate:SSO
For reference: There are more than 3000 EventNames which you can find on:
https://gist.github.com/pkazi/8b5a1374771f6efa5d55b92d8835718c
This list of AWS EventNames is to be added in /var/ossec/etc/lists/amazon/aws-EventNames.
For the new setting to take effect we need to restart the Wazuh manager.
service wazuh-manager restart
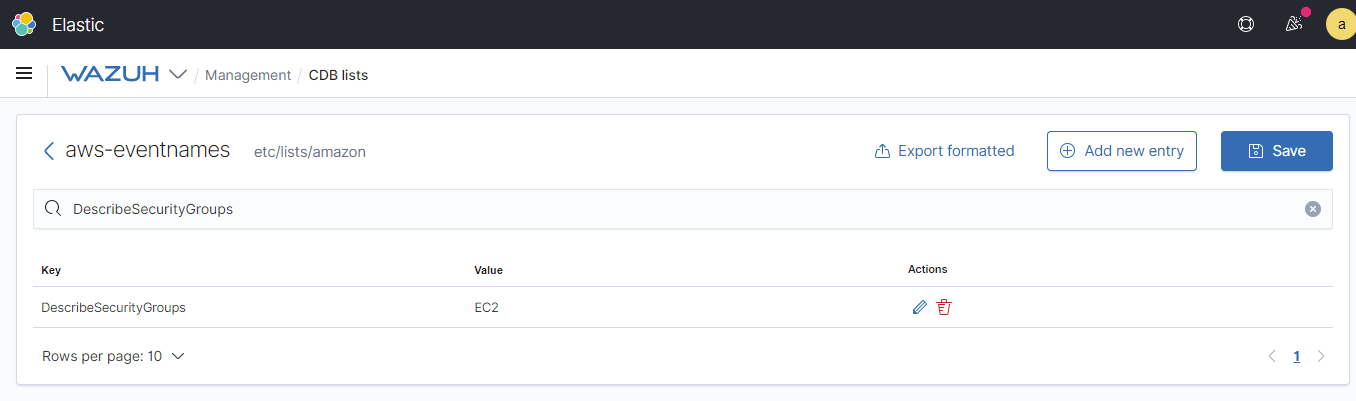

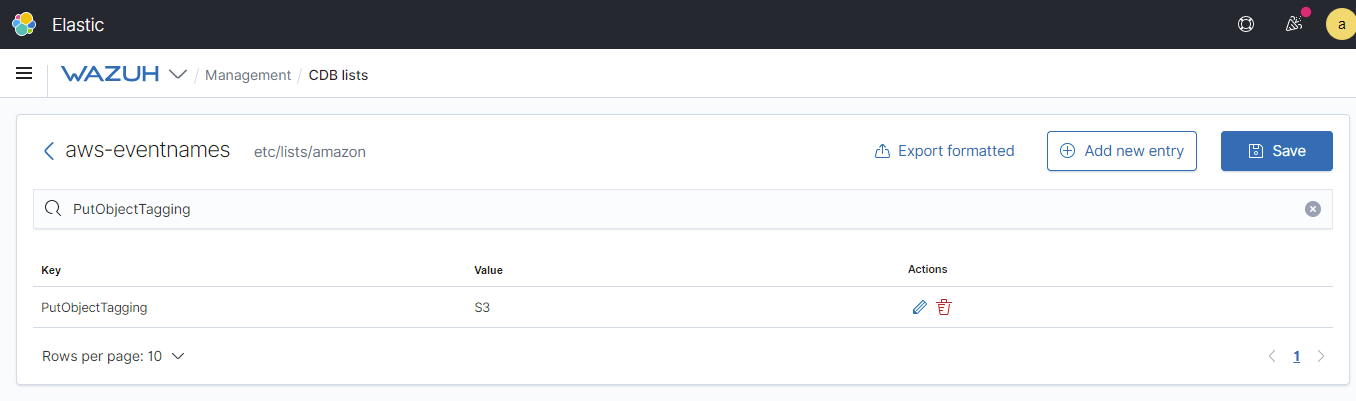
We can see here, the changes from the additional list in the aws-EventNames file now reflects in the list.
With the help of this decoders and rules, we will get our events triggered and we will find it under the Security Events.
<decoder name="json">
<prematch>^{\s*"</prematch>
<plugin_decoder>JSON_Decoder</plugin_decoder>
</decoder>
<group name="amazon,aws,">
<!-- AWS wodle -->
<rule id="80200" level="0">
<decoded_as>json</decoded_as>
<field name="integration">aws</field>
<description>AWS alert.</description>
<options>no_full_log</options>
</rule>
<!-- Cloudtrail -->
<!-- Filter by eventName: etc/lists/amazon/aws-eventnames -->
<rule id="80202" level="3">
<if_sid>80200</if_sid>
<field name="aws.source">cloudtrail</field>
<list field="aws.eventName" lookup="match_key">etc/lists/amazon/aws-eventnames</list>
<description>AWS Cloudtrail: $(aws.eventSource) - $(aws.eventName).</description>
<group>aws_cloudtrail,pci_dss_10.6.1,gdpr_IV_35.7.d,hipaa_164.312.b,nist_800_53_AU.6,tsc_CC7.2,tsc_CC7.3,</group>
<options>no_full_log</options>
</rule>
<!-- If there is an error code: increase the level and change description -->
<rule id="80203" level="4">
<if_sid>80202</if_sid>
<field name="aws.errorCode">\.+</field>
<description>AWS Cloudtrail: $(aws.eventSource) - $(aws.eventName). Error: $(aws.errorCode).</description>
<group>aws_cloudtrail,pci_dss_10.6.1,amazon-error,gdpr_IV_35.7.d,hipaa_164.312.b,nist_800_53_AU.6,tsc_CC7.2,tsc_CC7.3,</group>
<options>no_full_log</options>
</rule>
<!-- Specific rules -->
<!-- Events with errors -->
<rule id="80250" level="5">
<if_sid>80203</if_sid>
<field name="aws.errorCode">AccessDenied</field>
<description>AWS Cloudtrail: $(aws.eventSource) - $(aws.eventName). Error: $(aws.errorCode).</description>
<group>aws_cloudtrail,pci_dss_10.6.1,pci_dss_10.2.4,pci_dss_10.2.5,gdpr_IV_35.7.d,gdpr_IV_32.2,hipaa_164.312.b,nist_800_53_AU.6,nist_800_53_AU.14,nist_800_53_AC.7,tsc_CC7.2,tsc_CC7.3,tsc_CC6.1,tsc_CC6.8,</group>
<options>no_full_log</options>
</rule>
<!-- Events with no errors -->
<rule id="80251" level="3">
<if_sid>80202</if_sid>
<field name="aws.eventName">DeleteObjects</field>
<description>AWS Cloudtrail: $(aws.eventSource) - $(aws.eventName).</description>
<group>aws_cloudtrail,pci_dss_10.6.1,gdpr_IV_35.7.d,hipaa_164.312.b,nist_800_53_AU.6,tsc_CC7.2,tsc_CC7.3,</group>
<options>no_full_log</options>
</rule>
<rule id="80252" level="10" frequency="22" timeframe="600">
<if_matched_sid>80251</if_matched_sid>
<description>AWS Cloudtrail: $(aws.eventSource) - $(aws.eventName) - high number of deleted object.</description>
<mitre>
<id>T1485</id>
</mitre>
<group>aws_cloudtrail,pci_dss_10.6.1,gdpr_IV_35.7.d,hipaa_164.312.b,nist_800_53_AU.6,tsc_CC7.2,tsc_CC7.3,</group>
<options>no_full_log</options>
</rule>
<!-- Logins -->
<rule id="80253" level="3">
<if_sid>80202</if_sid>
<field name="aws.eventName">ConsoleLogin</field>
<description>AWS Cloudtrail: $(aws.eventSource) - $(aws.eventName) - User Login Success.</description>
<mitre>
<id>T1078</id>
</mitre>
<group>aws_cloudtrail,authentication_success,pci_dss_10.2.5,gdpr_IV_32.2,hipaa_164.312.b,nist_800_53_AU.14,nist_800_53_AC.7,tsc_CC6.8,tsc_CC7.2,tsc_CC7.3,</group>
<options>no_full_log</options>
</rule>
<rule id="80254" level="5">
<if_sid>80253</if_sid>
<field name="aws.responseElements.ConsoleLogin">Failure</field>
<description>AWS Cloudtrail: $(aws.eventSource) - $(aws.eventName) - User Login failed.</description>
<group>aws_cloudtrail,authentication_failed,pci_dss_10.2.4,pci_dss_10.2.5,gdpr_IV_35.7.d,gdpr_IV_32.2,hipaa_164.312.b,nist_800_53_AU.14,nist_800_53_AC.7,tsc_CC6.1,tsc_CC6.8,tsc_CC7.2,tsc_CC7.3,</group>
<options>no_full_log</options>
</rule>
<rule id="80255" level="10" frequency="6" timeframe="360">
<if_matched_sid>80254</if_matched_sid>
<description>AWS Cloudtrail: $(aws.eventSource) - $(aws.eventName) - Possible breaking attempt (high number of login attempts).</description>
<mitre>
<id>T1110</id>
</mitre>
<group>aws_cloudtrail,authentication_failures,pci_dss_11.4,pci_dss_10.2.4,pci_dss_10.2.5,gdpr_IV_35.7.d,gdpr_IV_32.2,hipaa_164.312.b,nist_800_53_SI.4,nist_800_53_AU.14,nist_800_53_AC.7,tsc_CC6.1,tsc_CC6.8,tsc_CC7.2,tsc_CC7.3,</group>
<options>no_full_log</options>
</rule>
</group>
Login to your Invinsense Portal and open Wazuh
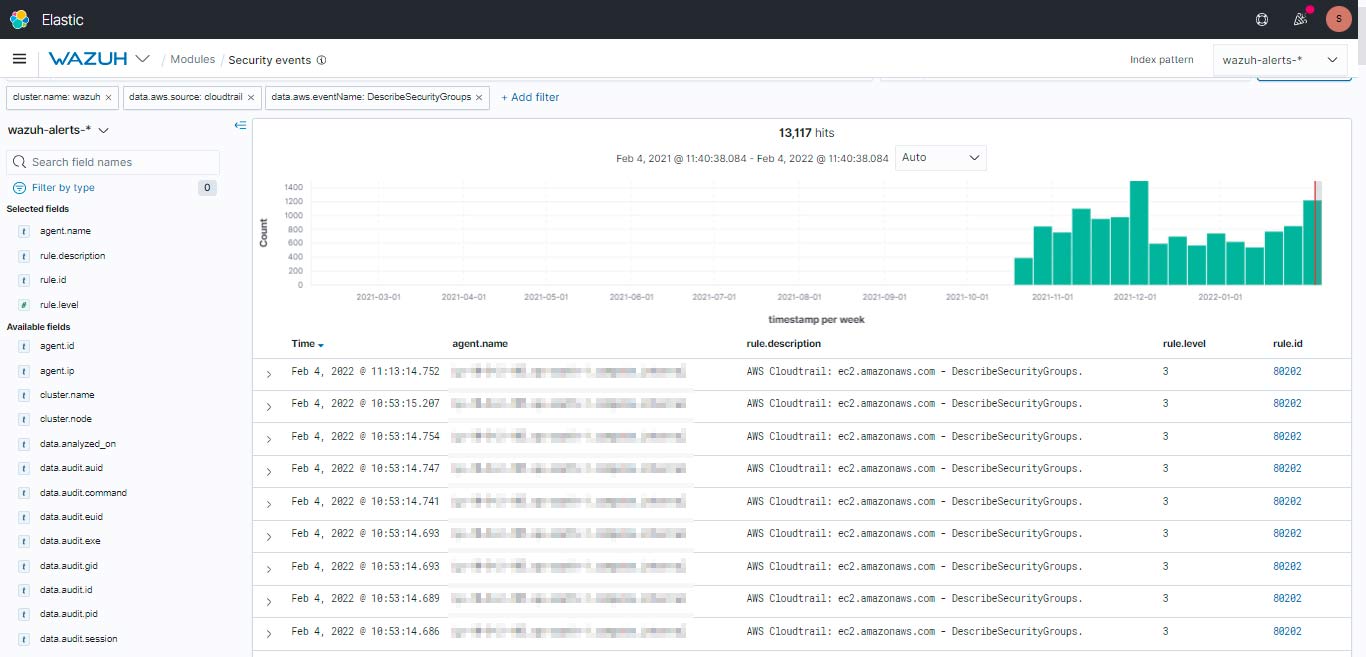
Here are the events which you can see in the Security Events for monitoring.
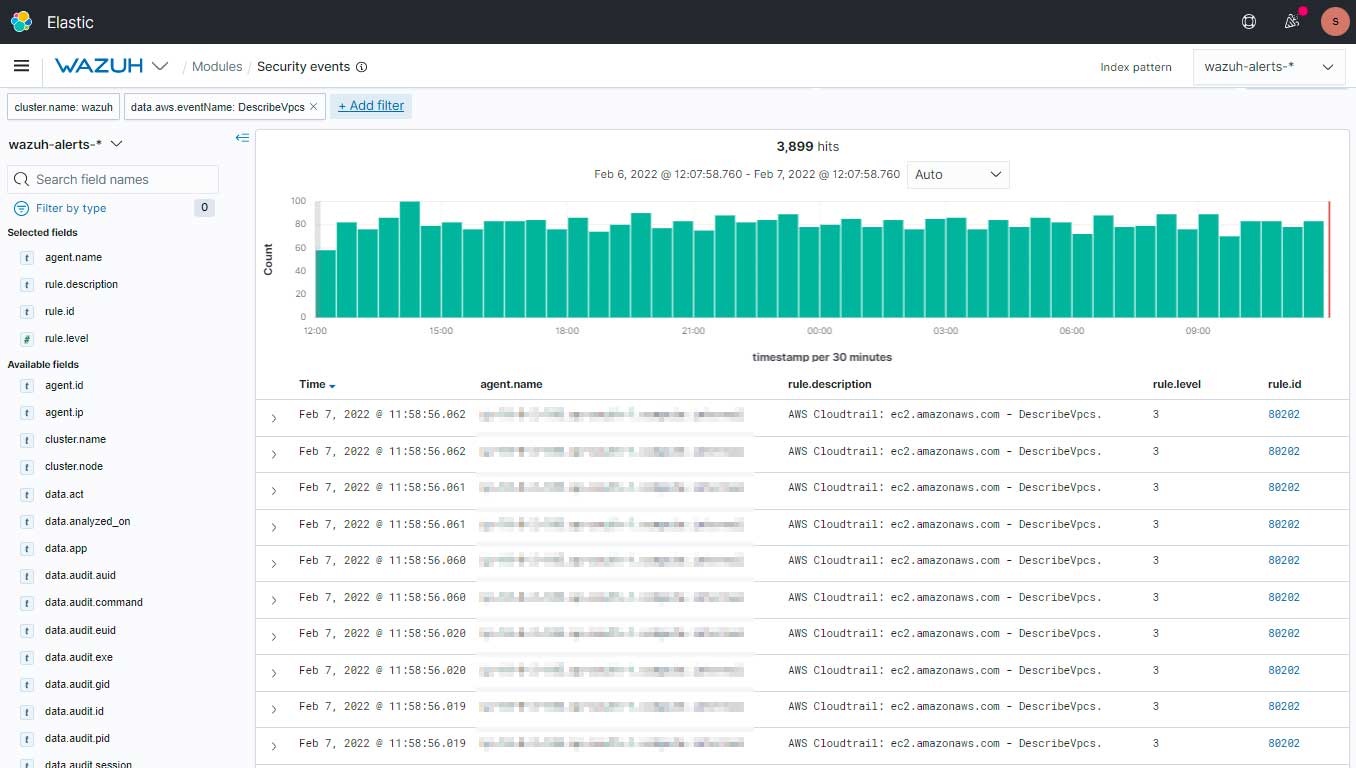
Conclusion
Using Wazuh and CloudTrail, we can reduce the signal-to-noise ratio and this is how we will get the AWS EventNames events in the security events and catch if any suspicious event that has occurred.





