Bitcoin Abuse
On December 1, 2023
What is BitcoinAbuse?
BitcoinAbuse is a platform that collects and analyzes data related to bitcoin scams, thefts, and other malicious activities on the Bitcoin network. Wazuh is an open-source security monitoring solution that can be used to detect and respond to security threats. In this article, we will discuss the integration of BitcoinAbuse with Wazuh.
Architecture of BitcoinAbuse:
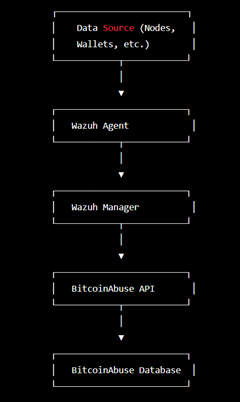
In this architecture, data is collected from Bitcoin nodes, wallets, and other sources using Wazuh agents. The Wazuh Manager then collects, normalizes, and analyzes this data to identify patterns of suspicious activity related to Bitcoin. The analysis results are sent to the BitcoinAbuse API, which uses machine learning, data mining, and other techniques to identify potential Bitcoin-related security threats. The results are then stored in the BitcoinAbuse database for further analysis and reporting.
Overall, this architecture provides a powerful tool for detecting and responding to Bitcoin-related security threats, such as scams, thefts, and other malicious activities. By integrating BitcoinAbuse with Wazuh, organizations can better protect themselves and their customers from the risks associated with Bitcoin.
Integration Steps from BitcoinAbuse to Wazuh:
BitcoinAbuse is a platform that collects and analyzes data related to bitcoin scams, thefts, and other malicious activities on the Bitcoin network. Wazuh is an open-source security monitoring solution that can be used to detect and respond to security threats. In this article, we will discuss the integration of BitcoinAbuse with Wazuh.
Integration Steps:
1. Configure Wazuh to collect log data related to Bitcoin transactions.
To integrate BitcoinAbuse with Wazuh, we need to configure Wazuh to collect log data related to Bitcoin transactions. This can be done by configuring Wazuh to monitor Bitcoin nodes or wallets and collect log data from them. The log data can include information such as Bitcoin addresses, transaction IDs, and amounts.
2. Send log data to the BitcoinAbuse API for analysis.
Once the log data is collected, we need to send it to the BitcoinAbuse API for analysis. The BitcoinAbuse API provides a REST interface for submitting Bitcoin addresses and transaction IDs for analysis. We can use the API to submit the log data collected by Wazuh for analysis.
3. Analyze log data using BitcoinAbuse.
Once the log data is submitted to the BitcoinAbuse API, it is analyzed using the platform’s algorithms and data processing pipeline. BitcoinAbuse uses a combination of machine learning, data mining, and other techniques to identify patterns of malicious activity on the Bitcoin network. The analysis results are stored in the BitcoinAbuse database and can be accessed through the platform’s web application.
For integrating BitcoinAbuse with Wazuh, we can start by configuring Wazuh to collect log data from a test Bitcoin network. We can then send the log data to the BitcoinAbuse API for analysis and view the results in the platform’s web application.
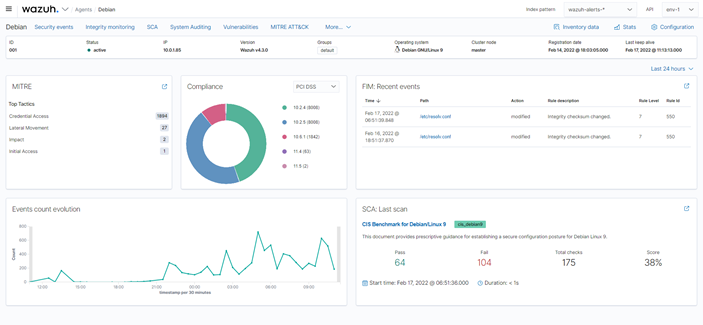
Use case & Dashboard:
Prevention:
Preventing Bitcoin abuse can be challenging, but there are several steps you can take to reduce the risk of becoming a victim of Bitcoin scams, thefts, and other malicious activities. Here are some tips for preventing Bitcoin abuse:
• Educate yourself about Bitcoin and its risks: Bitcoin is a relatively new and complex technology, and it’s important to understand how it works and what the risks are.
• Use reputable Bitcoin services: When buying, selling, or storing Bitcoin, it’s important to use reputable Bitcoin services that have a proven track record of security and reliability.
• Be cautious of unsolicited offers and scams: Bitcoin scams are prevalent, and scammers often use unsolicited offers to lure victims into giving up their Bitcoin.
• Keep your Bitcoin safe: Storing Bitcoin safely is critical to preventing theft and other malicious activities. Use a hardware wallet to store your Bitcoin offline, and never share your private keys or passwords with anyone.
• Report suspicious activity: If you notice any suspicious activity related to Bitcoin, such as phishing sites, scam sites, or other Bitcoin-related blacklists, report it to BitcoinAbuse or other relevant authorities.
• Use anti-malware software: Malware is a common tool used by hackers to steal Bitcoin, so it’s important to use anti-malware software to protect your computer and mobile devices.
Conclusion:
The integration of BitcoinAbuse with Wazuh provides a powerful tool for detecting and responding to Bitcoin-related security threats. By collecting and analyzing log data from Bitcoin nodes and wallets, we can identify patterns of malicious activity and prevent fraud and theft on the Bitcoin network. The integration can be customized to meet the specific needs of different organizations, such as financial institutions and law enforcement agencies.





