AWS Security’s Best Practices to reduce Risks
On March 16, 2015
Understand the Shared Responsibility Model:
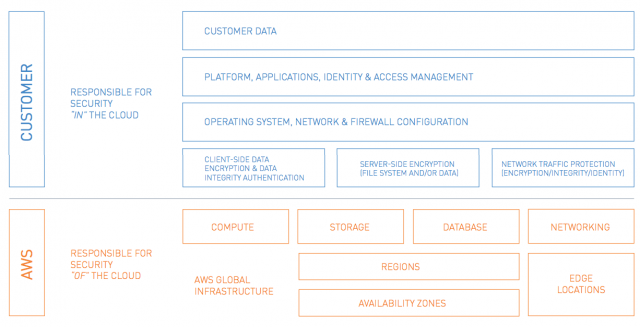
Amazon Web Services (AWS) follows a shared responsibility model. Amazon takes responsibility for the security of its infrastructure, and has made platform security a priority to protect customers’ critical data and applications. Amazon detects fraud and abuse, and responds to incidents by notifying customers. Customers are also responsible for the application hosted in AWS & security configurations done in AWS services.
Enable CloudTrail:
CloudTrail is an AWS service that generates log files of all API calls made within AWS, including the AWS management console, SDKs, command line tools, etc. This capability allows organizations to continuously monitor activities in AWS for compliance auditing and post-incident forensic investigations.To Secure AWS account, below cloudtrail points should be enabled
- Enable Cloudtrail in all Regions.
- Turn on Log Validation so that any changes in the logs file store in S3 bucket will be notified.
- Turn on multi-factor authentication (MFA) to delete CloudTrail S3 buckets, and encrypt all CloudTrail log files in flight and at rest.
Follow IAM best practices:
IAM - Identity & Access Management is a web service which aims to enable secured control access to AWS resources. IAM is used to control who is authenticated and who is authorized to use the resources. Some of the steps taken for a strong IAM framework are listed below.
- Do not Use Access keys for root users
- Create Individual IAM users
- Provide least privileges
- Use Customer managed key and AWS managed key.
- Configure strong password policies
- Enable MFA for privileged user
- Use Roles for Application that runs on EC2
- Do not Share Access keys
- Rotate credentials regularly
- Monitor Activities on Your AWS Account
Follow Security best practices while using AWS database and storage services:
AWS provides many storage solutions like Object based storage - S3, Elastic Block Storage, Relational Database Service- RDS & Aurora, Data warehousing - Redshift, In-Cache memory - Elasticache and NoSQL - DynamoDB. Some steps that need to be taken to ensure secure storage are :
- Ensure that no buckets are publicly accessible
- Enable encryption of S3 bucket for security
- Enable encryption of RDS storage for security
- Restrict access to RDS instances to decrease the risk of malicious activities such as brute force attacks, SQL injections, or DoS attacks.
Enable Configure management:
AWS inspector, automatically assesses application vulnerability or deviations from best practices, including impacted networks, OS, and attached storage. AWS Config, is a service that identifies all of your AWS resources and then evaluates the same with the required AWS configuration needed for your setup.





