Executing the Attack
On June 8, 2018
In this article we’re going to see how to execute an arp spoof attack that will also lead to sniffing packets along with stealing credentials. So let’s get started without further ado …
NOTE: Please perform this attack on your own machines or use the VMware / Virtual Box.
Stuffs I’ll be using: –
- Windows Machine (Target/Victim)
- Kali Linux (Attacker)
- Ettercap (Tool present in kali for performing MITM attacks)
- Wireshark (Used for sniffing packets)
Both the machines are connected in a single network.
Steps:
Go to Kali Linux and click on the IP forwarding or you can drop all the packets between the target and the router.
Use the command to turn on IP Forwarding:
echo 1 > /proc/sys/net/ipv4/ip_forward
and again cross check it by the command:
cat /proc/sys/net/ipv4/ip_forward
Make sure the value is 1
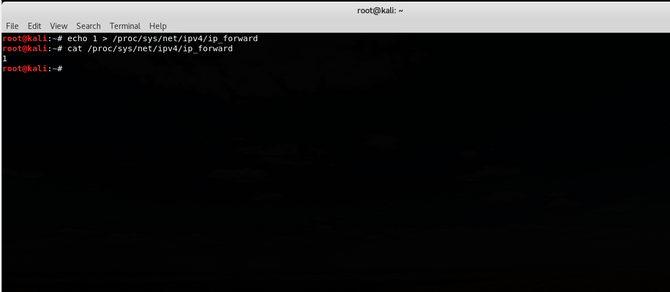
Check your router’s default gateway or IP using the following command: ip route
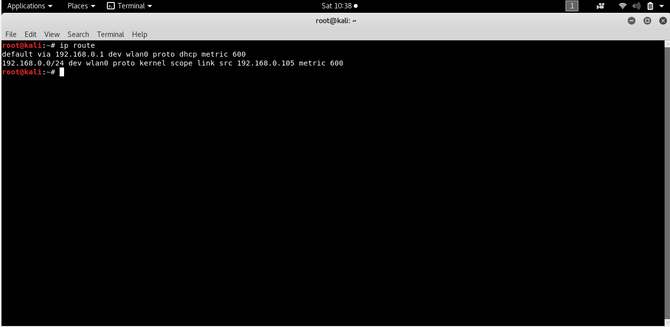
Go to your windows machine and open cmd by typing: and check your IP address: ipconfig
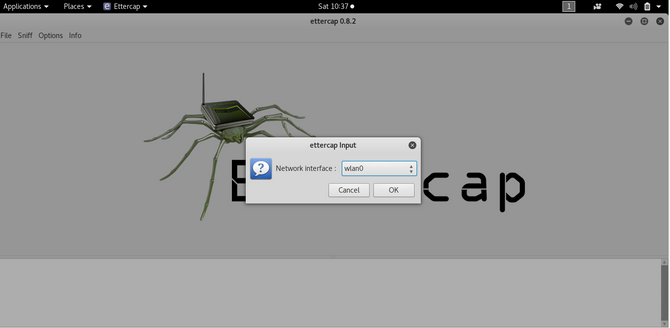
Start the Ettercap tool GUI by typing: ettercap –G
Go to the tab and click the button Unified Sniffing

You will then be asked to choose your own network adapter for the network adapter. In my case, their wlan0 as I use the wireless network card of my KALI.
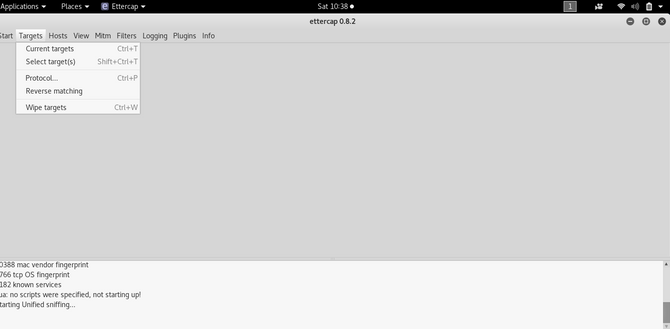
Click on Targets tab and select Current targets.
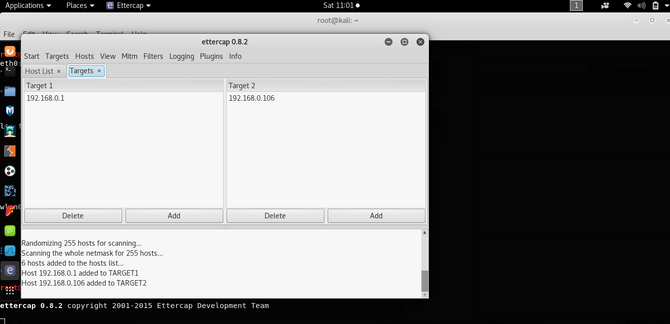
In place of target 1 add the IP address of the default gateway and in the place of target 2 add the IP address of the target (Windows machine).
Click on the MITM tab and select arp poisoning
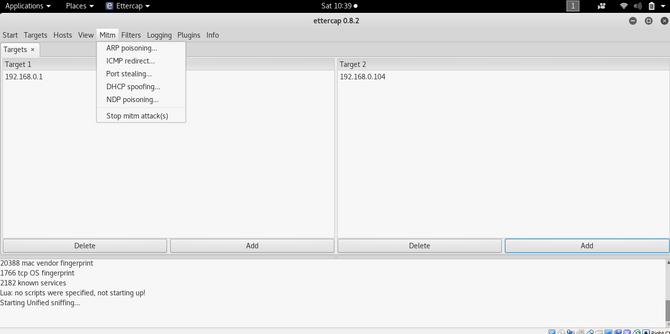
Now pick the remote connection for sniffing and then press all right.
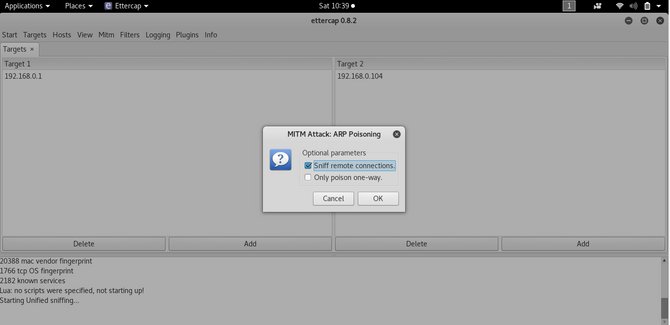
Now open Wireshark to sniff all of our target’s packets.
Choose your network interface after opening and press the Start button.
Go to your windows machine now and try logging into any website.
Come back to Wireshark and try using filters like ip.addr == 192.168.0.106(target’s IP address) to show all packets related to our target only.
Now search for the packets for any sensitive information, but most passwords are sent in post requests so try to search for any post requests and if you’re lucky you might get something like that?
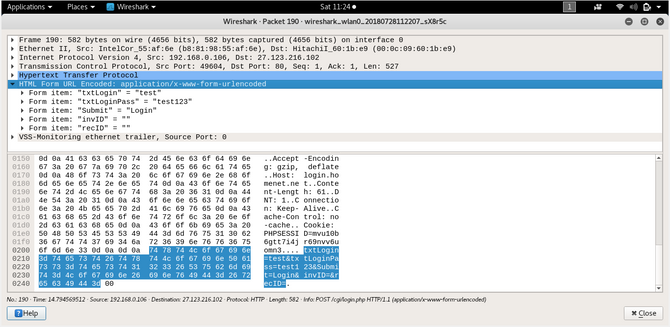
So that’s for now. See you next time.





