Invinsense Cybersecurity Platform
On January 27, 2021
Introduction to Invinsense Platform:
Growingly we have started observing that there is no one integrated platform that addresses one of the key problems faced by any organization today; how to put in an Offensive & Defensive Strategy to combat cyber security threats. We have Offensive strategies and technologies as well as Defensive techniques available. But, what is missing is a coercive approach as well as a platform that addresses both these areas in one tightly integrated platform.
To address these concerns, we have developed an Open-Source Based Invinsense platform that addresses the following areas in a seamless integration of strategy, services and solutions.
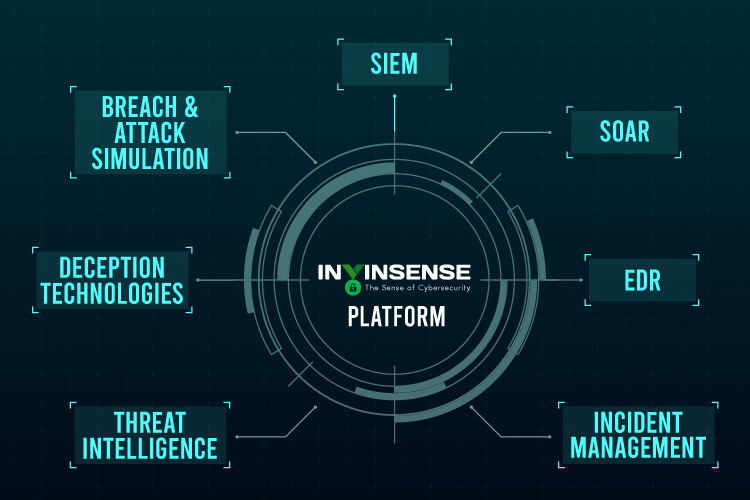
Key Areas integrated within the Invinsense platform:
SIEM – Security Information and Event Management: - This is where Log Retention and Analysis, Correlation, alerts etc. are managed
SOAR – Security Orchestration, Orchestration, Automation and Response: - This is the heart of the platform where the intelligence to take the correction actions, automation of run books, alert generation, trigger for incident management etc. happen
EDR – Endpoint Detection and Response: - This is a vital link to the overall process where the endpoints are monitored on real-time basis to detect any respond to any incidents
Incident Management: - The trigger to the incident management process where the incidents are detected, analyzed and responded comes from the SOAR engine. The actions in terms of response will follow the run book and will be logged and tracked with the ticketing tool and shall involve the security team.
Threat Intelligence: - This is what really helps the SOAR engine to make informed decisions in case of an incident. Threat intelligence feeds from various sources are analyzed and contextualized by the Automation engine to arrive at the incident response.
Deception Technologies: - These are real offensive techniques used to lure the attackers to commit mistakes and detect them as they enter the network.
Breach & Attack Simulation: - The approach is to simulate various breach scenarios on an ongoing basis, thereby evaluating the control gaps within the environment and remediating those real-time.
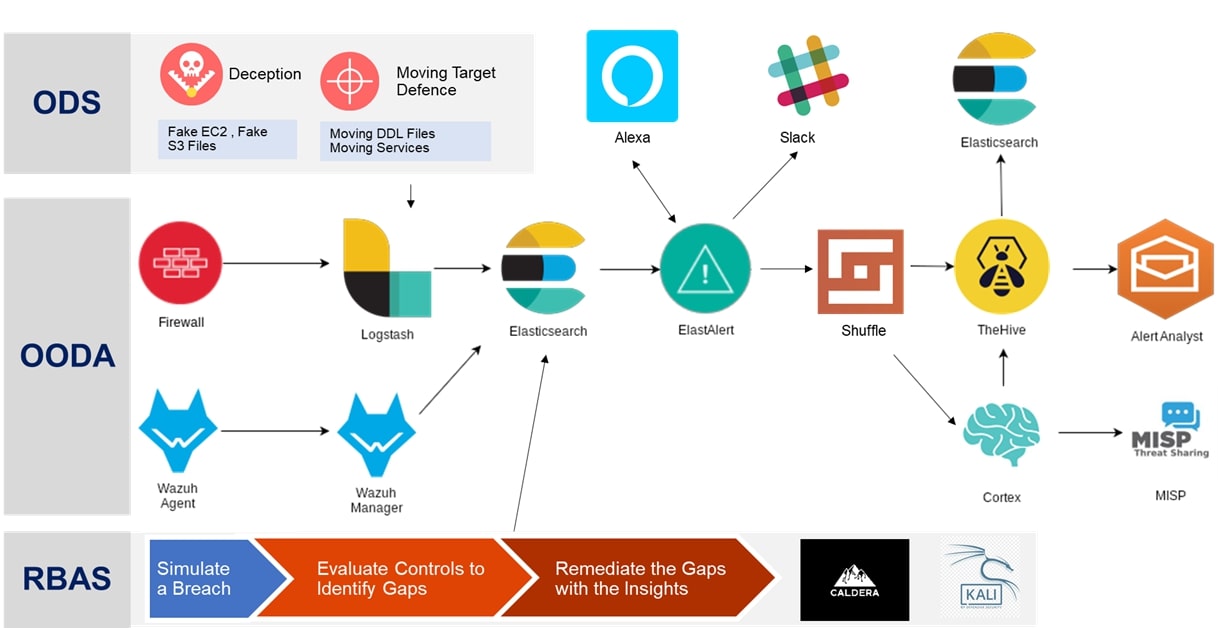
‘Wazuh’ is the Log collection and Correlation engine that sends alerts to Shuffle, which acts as the SOAR engine at the core of the Invinsense. ‘Shuffle’ does the orchestration and automation in conjunction with the Threat Intelligence platforms ‘Cortex’ and ‘MISP’. Once the incident is identified and analyzed, an alert is created for further action through the ticketing tool called ‘The Hive’.
We perform Breach & Attack Simulation exercises on an ongoing basis through the ‘Infection Monkey’ solution. ‘Déjà vu’ helps in putting a strategy for Deception Technologies and Moving Target Defense. With the might of this tighter integration of Strategy, Solutions and Services, we achieve an Offensive Defensive Strategy to combat Cyber Threats on a real-time basis.
Invinsense Components:
Wazuh Wazuh is the open-source security monitoring solution which collects and analyzes host security data. The Wazuh server component integrates closely with Elasticsearch and Kibana while the agent is capable of many security related tasks such as log analysis, rootkit detection, listening port detection, and file integrity monitoring. For this project we’ll utilize these capabilities to generate alerts.
Elasticsearch Elasticsearch will act as our log repository. It’s incredibly powerful and versatile, and when coupled with Logstash for log ingestion and Kibana for visualization, provides a robust platform for all types of data.
ElastAlert ElastAlert is an open-source project that provides an alerting mechanism for Elasticsearch. It simply queries Elasticsearch through the REST API and has numerous outputs to alert on a match. One of those outputs will feed the information into The Hive and another to Shuffle. This is how we distinguish the noise from the important events in the logs and generate alerts.
Shuffle Shuffle is an Open Source SOAR engine that acts as the core of the Invinsense platform. The central hub that communicates with Wazuh, Cortex, TheHive and any other tool is the automation and orchestration engine called Shuffle. Shuffle plays a vital role in the overall integration.
The Hive The Hive is an alert management platform used for managing an incident alert from creation to closure.
Cortex Cortex is a Threat Intelligence Platform that allows the use of “analysers” to gain additional information on the indicators already present in your logs. It allows the querying of third-party services on indicators such as IP, URL, and file hash, and will tag the alert with this additional information.
MISP MISP is an open source threat sharing platform maintained by CIRCL which, among many other uses, allows the operator to subscribe to threat intelligence feeds. These feeds can either be paid subscriptions or community maintained feeds from various organizations, and are our primary source of data enrichment.
Dejavu DejaVu is an open source deception framework which can be used to deploy decoys across the infrastructure. This could be used by the defender to deploy multiple interactive decoys (HTTP Servers, SQL, SMB, FTP, SSH, client side – NBNS) strategically across their network on different VLANs. To ease the management of decoys, we have built a web based platform which can be used to deploy, administer and configure all the decoys effectively from a centralized console. Logging and alerting dashboard displays detailed information about the alerts generated and can be further configured on how these alerts should be handled.
Caldera The Caldera is an open source Breach and Attack Simulation (BAS) tool that assesses the resiliency of the customer environment to post-breach attacks and lateral movement.





