Malware behind the largest DDOS attack (Mirai Botnet)
On December 19, 2016
Mirai Botnet: A brief on one of the largest DDOS attacks in the history of Internet
Mirai Botnet came into light in October 2016 when it was responsible for a DDOS attack that took down many large websites like PayPal, Netflix, Spotify etc. So let’s go step by step
What is a DOS Attack?
A Denial of Service Attack is an attempt by momentarily bringing it down to its intended users to make the system or network resources inaccessible. This is achieved simply by overwhelming computer or network resources with a large quantity of unnecessary requests to overwhelm the program.
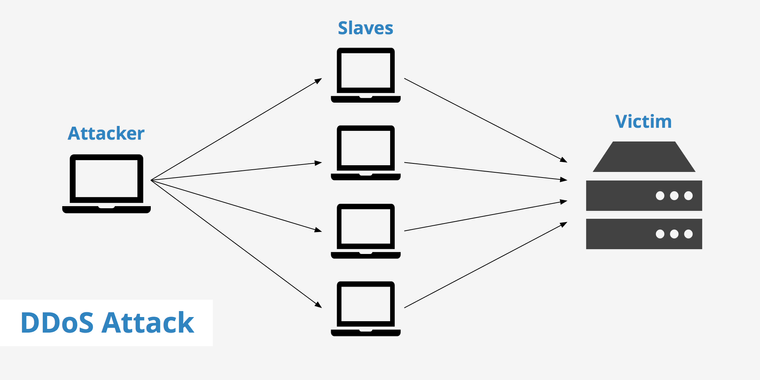
What is a DDOS Attack?
A DDOS is nothing but a DOS attack carried out from multiple sources to increase the effectiveness of the attack due to more requests being overwhelmed than a DOS attack.
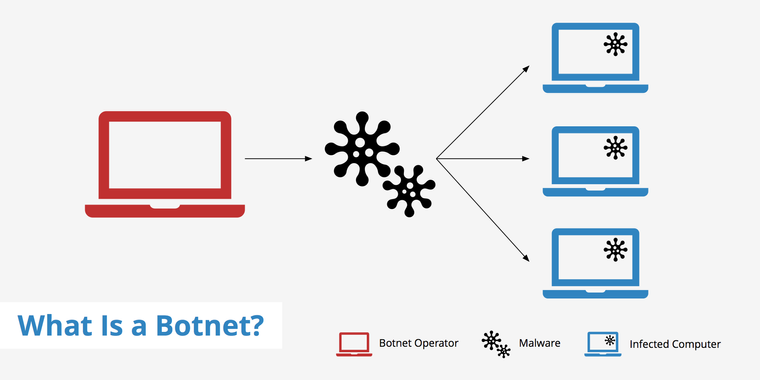
What is a Botnet?
Botnet is a collection or network of internet-connected devices infected with a specific form of malware and operated as a community without the knowledge of the target or the user. In plain terms, they are a group of bots or zombies that are remotely controlled for malicious purposes by an attacker as a group.
Mirai Botnet
With the rapid rise in the number of IOT devices which is estimated to reach around 30 billion by 2020, people would be too much dependent on these devices by then. If it’s a smart fridge or a baby tracking system or internet-controlled vehicles, they will certainly bring convenience and ease to our lives. Yet we, like all humans, still tend to overlook the security implications of these sophisticated internet-connected devices, and that’s exactly how mirai malware used these devices.
So first let’s understand what mirai is
Mirai is a malware that infects internet-connected devices operating on Linux OS to serve as zombies or bots that are later used as part of a botnet for a bigger fatal attack like DDOS attacks.

So How does Mirai malware attack?
What mirai does is searches for internet-based IOT devices that have open telnet ports (port 23), which is clearly an unencrypted communication channel and should not be favored if we have a secure communication channel like ssh.After searching for open telnet ports, it attempts to log in to the devices using a 61 username and password list/combos that are used on those devices by default and are never changed. After accessing the device, a program runs that takes control of the entire system and swips out any other malware if it is present in that device to assert the gadget as its own. Now that the attackers are breaching the machines effectively, they act as bots and become part of a botnet. Attackers use these botnets to perform a DDOS attack on a large scale. It therefore uses a very simple and ignored flaw in a very clever way rather than using a complex mechanism.
The Story
This deadly malware was developed by 3 American undergraduates according to resources. Prakash Jha, who was a Rutgers undergraduate, liked Minecraft very much. And there’s this Minecraft feature where people can earn money by hosting game servers from Minecraft. So hosts are conducting DDOS attacks on their competitors to put their servers down and thus draw their own company.
Which contributed to Paras Jha, Josiah White, and Dalton Norman creating the Mirai botnet. Under the name “Anna-Senpai,” Jha posted it online and named it Mirai after Mirai Nikki’s anime series as he loved watching anime. But according to an FBI agent who invested this attack gave the following statement “These kids are super smart, but they didn’t do anything high level—they just had a good idea”
The Attack
The first attack came on September 19, 2016, which was carried out on OVH, which is a cloud computing provider, and the explanation was that it hosted some kind of resources normally used by the Minecraft server hosts to counter DDOS attacks.
Then Jha made the malware’s source code online under the name “Anna-Senpai,” resulting in another attack after a month.
A large-scale DDOS attack on DYN, which is a DNS service firm by some other hacktivist community, was carried out on October 21, 2016. The consequence was that most internet channels and utilities in Europe and North America were inaccessible to consumers.
The three Americans were found guilty in December 2016 and were found to be responsible for the Mirai Botnet-related attacks.
Protection from these kind of attacks
Well, there’s not much you could do, but since the mirari botnet cleverly used a very common overlooked weakness, what you could and should always do is to change your internet connected devices ’ default credentials from the very first day. Furthermore, if you own a lot of internet connected devices, it is always recommended to put a firewall because it gives your devices an extra layer of security.
So that’s for now. See you next time.





