Phishing - A Game of Deception
On October 23, 2021
Phishing defined
Phishing, a type of social engineering, is defined as the act of sending out fraudulent emails to unsuspecting victims and inducing them to reveal their confidential information such as passwords or credit card details. It is the most common form of cyber crime and dangerous as well, because it goes undetected by regular anti-virus software.
How does it work?
- Step 1
Phishers use multiple platforms such as messages, emails or phone calls to lure victims.. They choose their targets, collect information about them, and decide on the attack strategies. - Step 2
Next, they create pages with fake urls or send phony emails to the targeted victims to collect information. - Step 3
The messages that the phishers send usually appear trustworthy and genuine thus giving way to a higher attack probability. - Step 4
If the attack was successful, phishers will monitor and collect the data provided by the victims. - Step 5
Finally, the attackers use this data to make illegal transactions or commit fraudulent acts.
Dangers of Phishing
The employee is the first line of defense. If the target is an employee of an organization, then the whole organization is at risk of losing millions of dollars, especially if the attack has been successful. A recent survey estimated that a breach costs a company $3.86 millions on an average. This could be high or low depending on the type and volume of data that was stolen.
In the case of an attack on an individual, all his bank accounts, loan accounts and other investments are compromised, as are his credit and identity information.
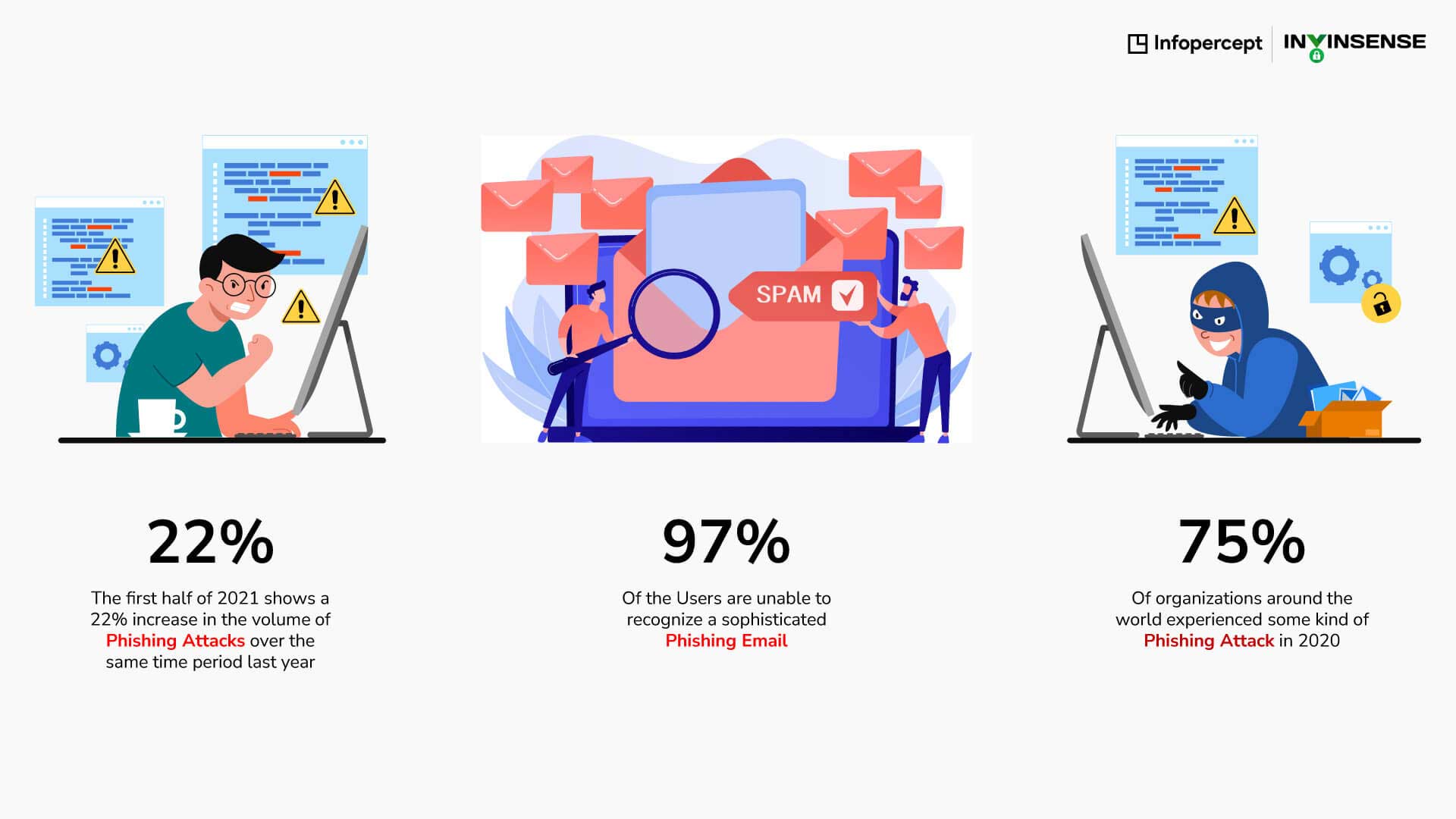
Alarming phishing statistics:
It is estimated that 14.5 billion spam emails are sent everyday! Nearly 97% of the users are unable to recognise a sophisticated phishing email.The first half of the year 2021 has seen a whopping 22% increase in the volume of phishing attacks over the same time period as of last year. 75% of organizations around the world have experienced phishing attacks in some form.
Types of Phishing
- Spear Phishing
A specific individual within an organization is targeted to steal his login credentials. He then uses the information such as name, designation and other contact information to send phishing emails. - Vishing
It is also known as voice phishing. Here the attacker tries to steal information over the phone, pretending to be a trusted friend, relative or their representative. - Email Phishing
This is one of the most common forms of attacks where the hacker sends a legitimate looking email designed to trick the user into giving out information either by clicking links or entering confidential data in a false site. - HTTPS Phishing
This happens when an unsuspecting person opens an email and clicks on a link to a false website. The site then captures the sensitive information. - Pharming
A malicious code is installed on the victim’s computer, which then directs him to a fake website designed to lure their confidential information. - Pop-up Phishing
Pop-ups occur frequently citing a problem with the computer’s security and tricking the user into clicking it. Upon clicking a malware is downloaded into the computer system triggering an attack. - Whaling
In this form of attack, a senior official within the organization is often targeted. This is done because the top official usually has access to very critical information and a successful attack can bring the organization on its knees.
Traditional Solutions to counter Phishing
Pause before clicking: On an individual level, it is prudent to be alert at all times and be educated on how phishing attacks look like. For instance, while receiving an email that prompts you to click on a link, it is wise to review the sender’s address and check for impersonations. Also check the domain name, if it is real or misspelled so cleverly that it often goes unnoticed. (e.g. “hbfcnetbanking.com”).
On a larger scale, such as in an organization, the entire workforce has to be made aware of the dangers of cyber attacks via training or mock demo sessions. When in doubt, always check with an IT team member. It pays to play safe.
Traditional Solutions to Phishing Attacks
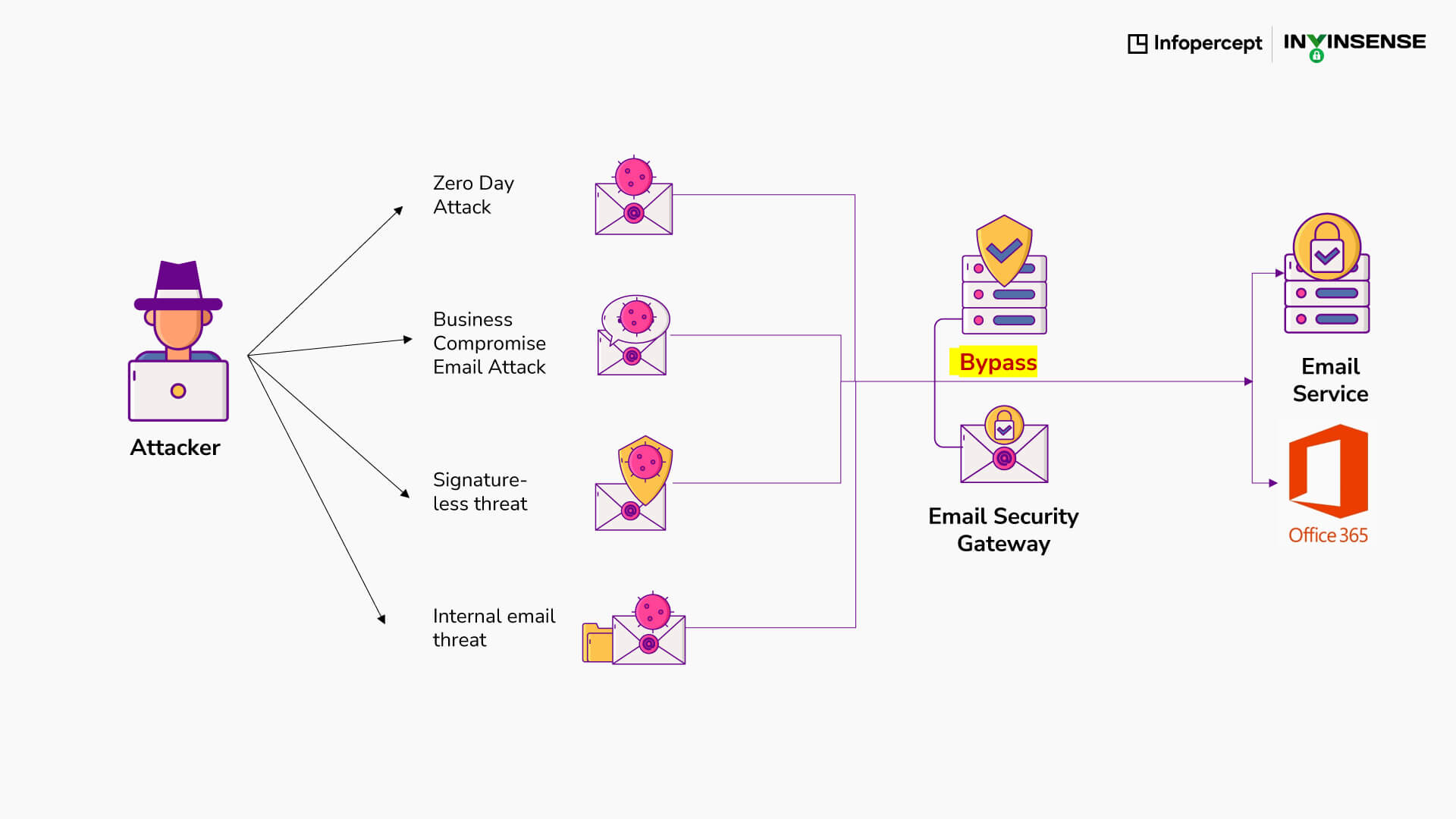
Tactics, Techniques, and Procedures (TTPs) are used within cyber intelligence strategies to identify threat patterns that are associated with a group of threat actors. They are often used by hackers to plan and execute cyber attacks on networks. They provide information about how to respond to breaches and prevent future ones. Analysis of such information often gives insight into the thinking and attack strategy of the hacker. This aids in counterintelligence and strategic security operations.
Often cyber security companies offer 99% protection from phishing attacks. Traditionally, solutions that were provided used known ids which were ineffective whereas the hackers attack by developing new types of content, new URLs, new IP addresses etc.
Sophisticated Email Phishing Detection and Prevention
Leveraging Open Source Deception, SIEM, SOAR, Threat Intel
Comprehensive Next Gen Managed SOC Phishing Solution by Infopercept
Personalized Threat Intelligence, Detection and Prevention
Threat Intelligence is often defined as the identification and analysis of cyber threats that are aimed at businesses. It involves examining huge amounts of data to filter out the relevant ones, spot the concerned areas, and deploy solutions to fix them. Now personalised threat intelligence goes a step further by giving context to the data. While the data generated draws out a map, threat intelligence draws out a route.
In order to meet your organization’s needs, it is imperative to check the three developmental stages of threat intelligence - producing, sharing, and applying.
- Producing threat intelligence requires an automation process that helps in easier categorization of the data. This helps analysts to research specific areas.
- Once the analyst is able to identify patterns in the raw data and able to draw conclusions, all is well. Now this has to be made actionable. For it to become actionable, it has to be done in a timely manner, it should be personalized and it has to be coherent.
- Final stage is that of applying. Figuring out who the intended audience is, and how the intelligence generated wil be used.
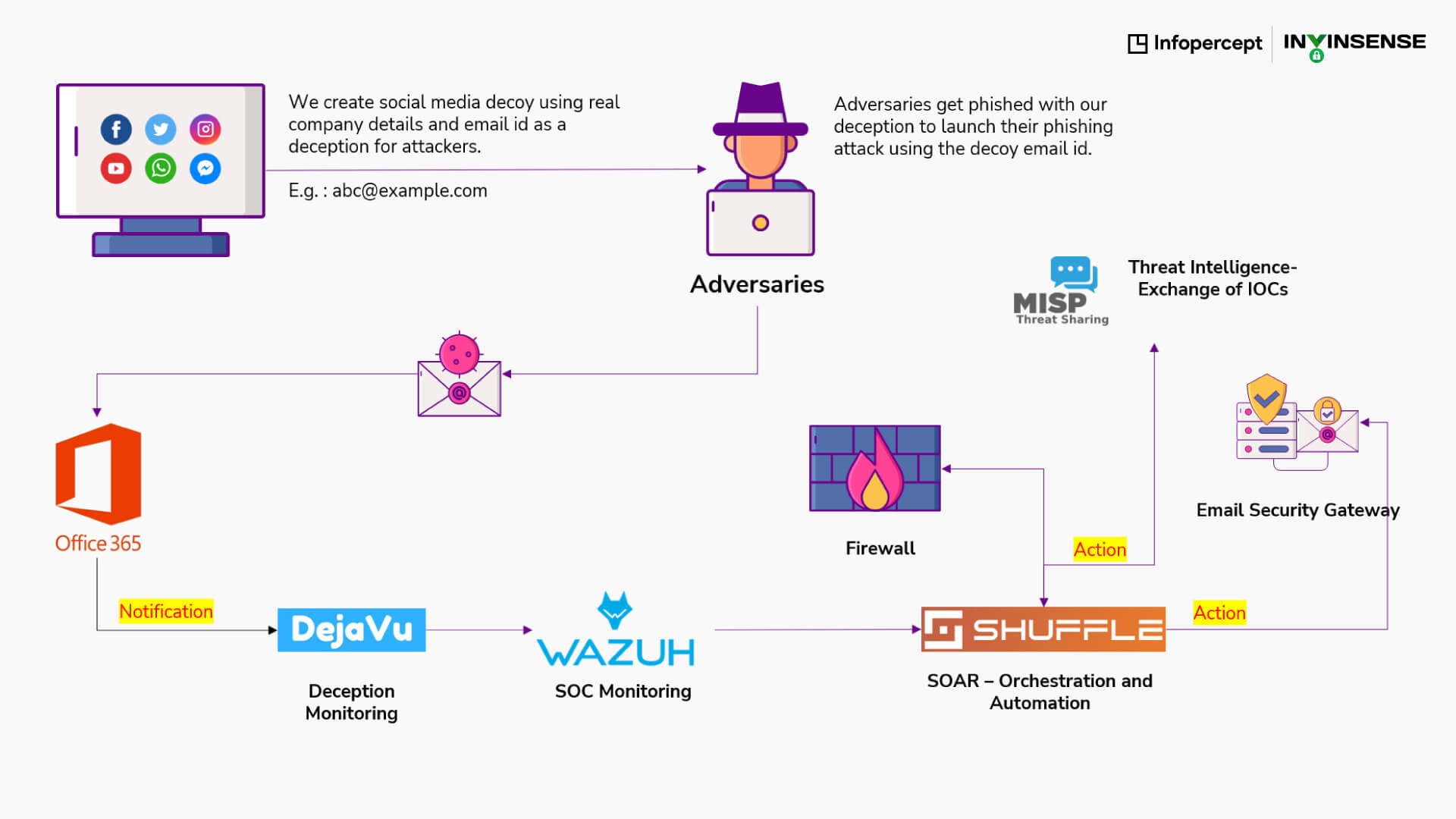
Infopercept beats the hackers at their own game; they lure the attackers by creating fake social media profiles/accounts using real company ids. e.g. abc@example.com
We create social media decoy using real company details and email id as a deception for attackers.
Adversaries get phished with our deception to launch their phishing attack using the decoy email id.
How does it work?
- Dejavu triggers an alert and sends it to Wazuh SIEM through syslog configuration.
- Integration of Wazuh SIEM is done with Shuffle.
- When an alert triggers in Wazuh from the Deception Email Client, it triggers the Shuffle Workflow.
- The system then starts analysis of the email header and IP Address.
- t pushes the IP address to MISP Threat Exchange Database for future reference and marks it as blacklisted.
- Creates a case in the Case Management Tool.
- Blocks IP Address in Email Security Gateway and Firewall
For cybersecurity to have upper hand, attacker sense is the most important approach. Like anti-phishing, in every counter, attackers’ tactics can be used to design and execute a proactive cybersecurity. Open source cybersecurity innovations help to leverage attacker intelligence to prepare counter cybersecurity intelligence.





