It's now more difficult than ever to meet the complex demands of compliance and security - especially with evolving threats, vague regulatory guidance, and limited resources. Due to lack of people involvement, organizations have not been able to effectively monitor and implement a proper measurement system. Organizations have been finding it difficult to adhere to different compliances with overloading documentation and improper integration of compliances and lean systems.
Improper integration of compliances and lean systems
Sample : Organization's Compliance Concerns
Multiple Compliance Requirements

Complex and Heavy system design

Policies being documented
not implemented

High Cost of Compliance

Fatigue in implementing systems

Multiple Risk
Assessment

How Infopercept Compliance Services Works
Infopercept strongly believes Compliance is an enabler of innovation. Infopercept's Compliance Optimization Services provide better ways to manage the burden that is compliance.
Imagine your organization's functions being aligned with the business objectives, where the processes are optimized and the procedures being automated with the assistance of data and technology. Your organization's controls would be predictive instead of reactive, since the compliance requirement would be met with efficiency. Your employees will derive more value from their roles and business will be secure knowing that its reputation is being protected and allowing the management to drive the business growth and innovation.
Our highly-trained & experienced Governance, Risk, Compliance, Process & Documentation Experts along with Virtual-CISOs take the guesswork out of protecting your valuable organizations. Infopercept with its highly skilled in-house consultants.
Compliance Expertize
ISO Standards
ISO 27001 | ISO 22301 | ISO 31000
Privacy
HIPAA | HITRUST | GDPR | GAPP
Regulatory
FEDRAMP | RBI | BNM | MAS | SAMA
Statutory
SOX | SOC 1 | SOC 2 | SOC 3
Regulatory
PCI-DSS | IT | DRP | BCPS

Infopercept's Compliance Optimization Services
Compliance Optimization Services come with a variety of default features and functionalities, all of which are included in our standard MSS offering:
- GAMEPLAN Shadow CISO
- Process Re-engineering
- Risk Management
- Process Excellence
- Compliances
- Technology Recommendations
- Random Spot Checks
- Management Review Meetings


With Infopercept's Compliance Optimization Services your organization can retain a board-level resource who can 'virtually sit inside your organization' and manage your security strategy, budget, review of risks and regulatory programs.
Infopercept will work with stakeholders such as the Shareholders, Board of Directors, Regulators, State Owned Enterprises, Publicly Listed and Private Entities, to improve their board and leadership's ethical and effective performance and organizational governance outcomes. By doing so Infopercept will ensure that your organization achieves ethical culture, exceptional performance, effective controls and legitimacy and further Infopercept will be able to deliver sustainable value over the long term.
Infopercept strongly believes that security strategies work best when they are risk-based and objective-driven. Rather than endless engagements with little or no progress, Infopercept will work with you to set a sensible roadmap of security objectives and predictably work through them over time. A good Governance, Risk, and Compliance (GRC) Program will protect your organization from Cyber Criminals.
ISO 27001 is globally recognized
Can you demonstrate to clients and stakeholders that your organization is managing information security risks?
ISO 27001 is a globally recognized, risk-based Information Security Management System, tailored to your operations.
Our experienced consultants ensure a cost-effective ISO 27001 journey. Let us help you become certified.
ISO/IEC 27001:2013 or ISO 27001 as it is commonly known, is an international Information Security Management System (ISMS) standard. It is a risk-based, robust framework that outlines the key processes and approaches business needs to manage information security risks, such as cyber-attacks and data breaches. It enables organizations to demonstrate to clients and internal and external stakeholders that their security and risk management approach meets industry best practice with respect to protecting data, such as financial information, intellectual property, employee details or information entrusted by third parties.
The information security standard spans all industries, highlighting best practices for improving the security of information and minimizing risks for businesses.
ISO 27001 also highlights how these practices can be refined, as information security needs develop in the future. Importantly, it adapts to your business as it changes.
The benefits of achieving ISO 27001
compliance?
More than ever, companies of all sizes are demanding this level of assurance from their suppliers. Consumers are also putting increased focus on information security and data protection. We can help you streamline processes to achieve operational efficiencies and help you prove your organization's commitment to cyber and information security and data protection.
Inspire Customer Trust
Being able to show compliance with the standard instils trust in customers and provides peace of mind to stakeholders, who can be sure that their information assets are handled, stored, and managed securely.
Show your commitment to
information security
Many businesses opt for the ISO 27001 certification because the framework is recognized at an international level. It helps organizations to effectively manage their global reputation for best practice information security management and gives them a competitive edge, not only nationally, but in alternative markets.
Minimize business risk
Embedding ISO 27001 into your organization will help to minimize the business risks around data breaches and cyber-attacks. This is especially important at a time when security breaches pose substantial legal, financial, and reputational risks.
ISO 27001 grows and changes with your business
The ISO 27001 framework is designed to grow with your business and focuses on the importance of taking a flexible approach to information security management.
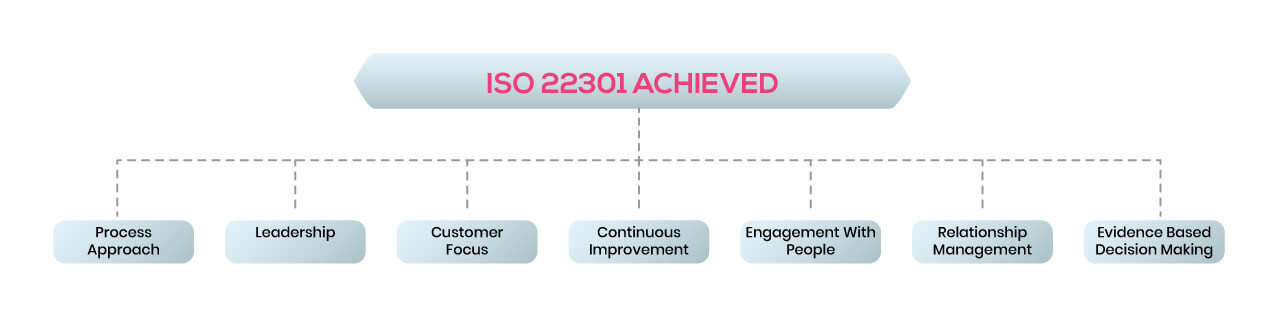
ISO 22301 is internationally recognized
Why Do You Need a Business Continuity Management System?
Disruption and a crisis can occur at any time. The inability to respond to a crisis or disruption can be costly and in some cases lethal to an organization.
ISO 22301 is the internationally recognized Business Continuity management (BCM) standard. The purpose of the Business Continuity Management System is to enable organizations to:
- Continually seek methods to eliminate and reduce risks, which will improve your performance now and in the future.
- Reassure your customers that you are putting business continuity issues high on your agenda to ensure seamless services.
- Provide regulators with assurance that you comply with appropriate legislation and other requirements that relate to Business Continuity.
The benefits of achieving ISO 22301
compliance ?
ISO 27001 Information Security Management System includes Annex A14 'Business Continuity Management', which can be expanded to meet the requirements of ISO 22301, which is easily aligned with other ISO Standards.
It Eliminates Risks
Eliminate and reduce risks and costs caused by crisis or disruption.
It Improves Performance
Improve your ability to respond to crisis and future disruptive events.
It Enhances Your Workers
Involve your workers in decision making and response to see positive results
Relationship to ISO 27001
ISO 27001 Information Security Management System includes Annex A14 'Business Continuity Management', which can be expanded to meet the requirements of ISO 22301, which is easily aligned with other ISO Standards.
ISO 22301 replaced the British standard BS 25999 as the framework for Business Continuity Management.
ISO 31000 Risk Management Consulting
ISO 31000 Risk Management Consulting helping you to manage your business risks. Organizations may face severe consequences in terms of economic performance and professional reputation, as well as environmental, safety and societal outcomes when they are unable to manage certain risks. Effective Risk Management helps organizations to perform well in an environment full of uncertainty.
Infopercept has been helping companies manage risk since it began and our leadership team have years of academic study and work experience on the subject.
Combined with our pragmatic approach to ISO standards, we can work with you to design and operate a Risk Management System that will meet your governance needs.
31000: 2018 - Risk management Guidelines provides a framework for development, maintenance and improvement of an effective risk management in organizations as well as in global supply chains.It is applicable for organizations of all sizes and industries.
ISO 31000 may not be well known but its philosophy can be seen across all the popular management system standards that are aligned to ISO's Annex SL format, such as ISO 27001, ISO 22301 and future versions of ISO 9001 and ISO 14001.
Being the international standard for Risk Management, we have long been passionate about the principles of ISO 31000 and the benefits that come with implementing it as part of another standard, or as a means of organizational risk governance.
Risk Management Principles
Key Themes of Risk Management
The standard starts with 11 Principles:
- Risk Management Creates and Protects
- Risk Management is an integral part of all organizational processes
- Risk Management is part of decision making
- Risk Management explicitly addresses uncertainty
- Risk Management is systematic, structured and timely
- Risk Management is based on the best available information
- Risk Management is tailored
- Risk Management takes human and cultural factors into account
- Risk Management is transparent and inclusive
- Risk Management is dynamic, iterative and responsive to change
- Risk Management facilitates continual improvement of the organization

The benefits of achieving ISO 31000 compliance?
- Identify & Control Risks.
- 11 Risk Principles.
- Provides Framework.
- Considers Context.
- Requires Management Mandate and Accountability.
- Continual Improvement.
- Integrate with other Annex SL based ISO standards.
Risk Management Framework
A "Mandate and Commitment" is required by management before creating the risk management framework, then as is becoming common in management system standards, a detailed understanding of the organization and its context is undertaken.
This helps to define the processes required, communication routes and reporting lines.
Risk Management Process
The risk management process focuses on the recognizable Identification, Analysis, Evaluation and Treatment of risk - which fits well with risk based standards such as ISO 27001 for Information Security.
Continual Improvement
The goal is to achieve continual improvement of the system by monitoring and reviewing activity.
Cybersecurity Maturity Model Certification
(CMMC)

Cybersecurity Maturity Model Certification
CMMC
The Cybersecurity Maturity Model Certification (CMMC) is a program initiated by the United States Department of Defense (DoD) in order to measure their defense contractors’ capabilities, readiness, and sophistication in the area of cybersecurity. The framework is a collection of processes, and other inputs from existing cybersecurity standards such as NIST, FAR, and DFARS.
The certification is applicable to both “prime” contractors who engage directly with DoD, and to subcontractors who contract with prime contractor to provide fulfilment and execution of those contracts. Although some level of certification is required of every contract beginning in 2026, DoD has indicated that they intend to issue contract opportunities at all levels of the maturity model. This means that there will be some number of requests issued that will require only a low level of certification, and some that will require higher levels of certification.
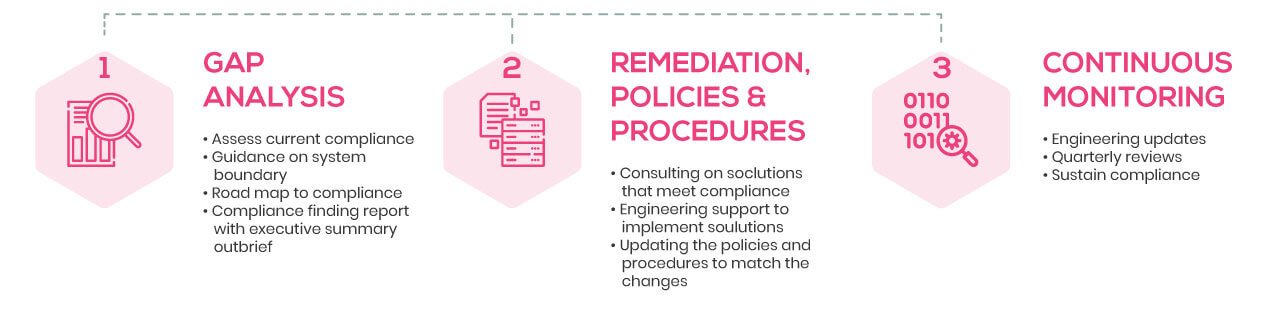
Infopercept helps you navigate CMMC requirements
While most compliance standards are assessed against an “in place” or “not in place” approach, CMMC not only addresses whether required controls are in place or not, but also requires various levels of maturity. CMMC has established five certification levels, each requiring a set of controls and associated maturity activities:
- Level 1 – Basic Cybersecurity Hygiene (Performed)
- Level 2 – Intermediate Cybersecurity Hygiene (Documented)
- Level 3 – Good Cybersecurity Hygiene (Managed)
- Level 4 – Proactive (Reviewed)
- Level 5 – Advanced/Progressive (Optimizing)
How can Infopercept support your business?
CMMC Advisory Services:
The Infopercept Consulting team will provide an initial assessment and then develop a gap analysis of your organization's maturity level in regard to CMMC certification. Our team then provides the required policies and procedures, develop a Plan of Action and Milestones (POA&M) for remediation purposes, and provides additional support to close remaining gaps. Our team practices a consulting approach that can be customized to support your needs and budget.
With support from Infopercept, you get the right inputs and insights into meeting the CMMC’s standards required for passing the certification assessment. Just as an auditor is required to look into your accounts, Infopercept will be available to meet your CMMC compliance and requirements and during its assessment.
CMMC Readiness Assessment
You can leverage Infopercept’s operational and consultative experience to help you reach the certification level needed to conduct your business. A CMMC Readiness Assessment follows a standardized and proven methodology that provides you with:
- The visibility to address areas in need of CMMC certification regardless of level.
- A comprehensive report that provides you with your current CMMC compliance status as well as recommendations for implementing and maintaining the required CMMC practices and processes.
Completion of our CMMC Readiness Assessment Service will additionally help you determine how to allocate resources to protect the confidentiality, integrity, and availability of Controlled Unclassified Information (CUI).
HIPAA
Health Insurance Portability and Accountability Act
If you hold protected health information for your clients, either in electronic (ePHI) or hard copy form (PHI), you must comply with the Health Insurance Portability and Accountability Act (HIPAA).
The Health Insurance Portability and Accountability Act (HIPAA) sets a national standard for the protection of consumers’ PHI by mandating risk management best practices and physical, administrative, and technical safeguards. HIPAA was established to provide greater transparency for individuals whose information may be at risk, and the Department of Health and Human Services’ Office for Civil Rights (OCR) enforces compliance with the HIPAA Privacy, Security, and Breach Notification Rules.
Protected Health Information (PHI)
The HIPAA Privacy Rule protects most “individually identifiable health information” held or transmitted by a covered entity or its business associate, in any form or medium, whether electronic, on paper, or oral. The Privacy Rule calls this information protected health information (PHI)
Who is Subject to HIPAA?
Up until 2009, the answer was Covered Entities, which are healthcare providers like doctors’ offices and hospitals. But when the HITECH Act passed, it expanded the oversight of the OCR to the Business Associates, which are the vendors who provide services to the Covered Entities Entities seeking to demonstrate HIPAA compliance to their customers and potential customers have several options available. The options in order of assurance range from; self-audits against the HIPAA requirements; to an independent HIPAA gap assessment and HIPAA Audit.
 CASE STUDY
CASE STUDY





