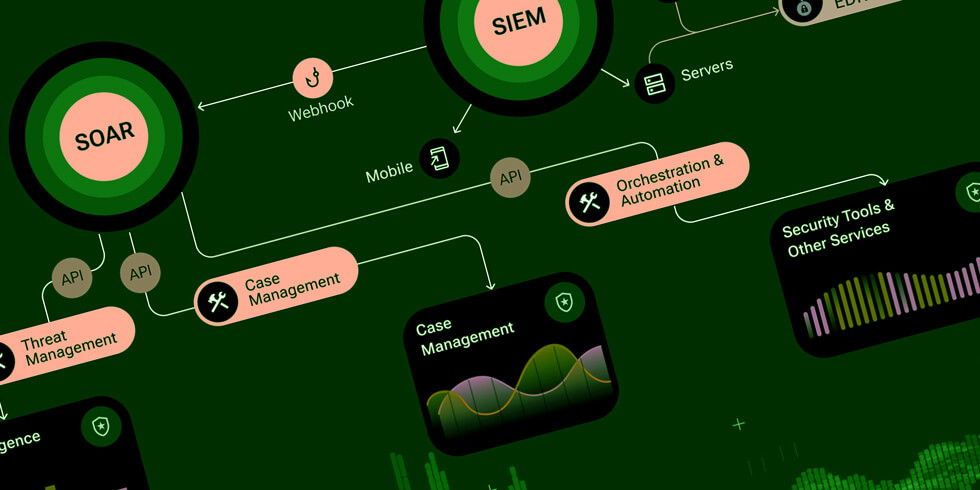
Security as a Code is the best way to ensure a series of security measures to protect your assets in the cloud. There are many advantages of utilizing code for security in the cloud.
Securing Infrastructure as a Code (IaC) in the cloud is critical to maintain a secured environment for your resources and data. It is also crucial for building various best practices for your cloud environment. Under this we help you take care of the below:
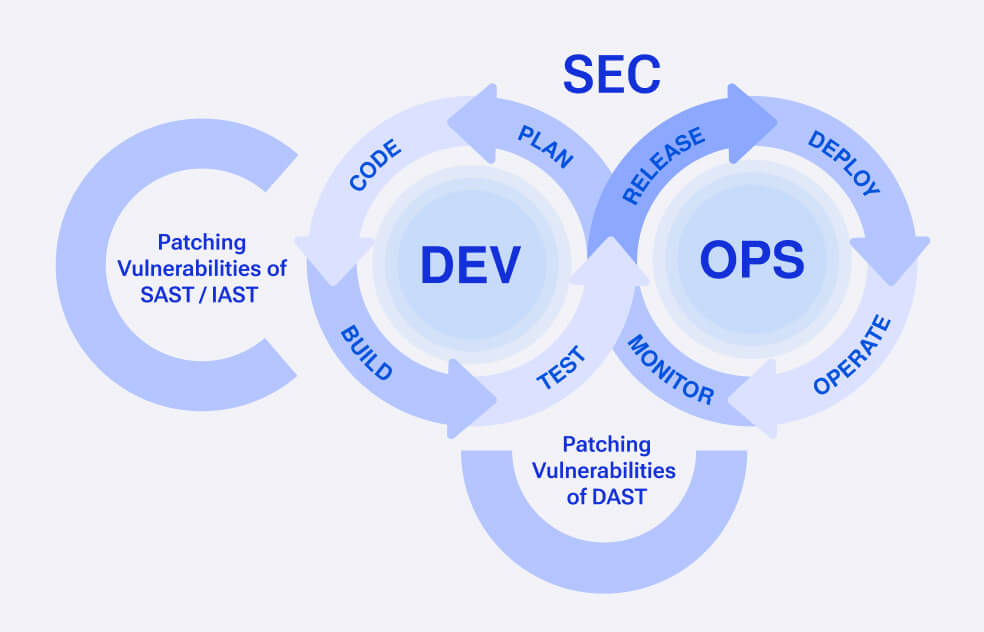
Cloud-native application development stands at the forefront of digital transformation's agility. While it accelerates development, it introduces complexities that challenge security teams. Invinsense DevSecOps harnesses a blend of culture, tools, and best practices to fortify applications and infrastructure, securing them from code to cloud.
Today, implementing DevSecOps isn't tough, but instilling
it with optimal practices and embedding it within
organizational culture remains a challenge. For instance,
DevSecOps aids in identifying vulnerabilities during Dynamic
Application Security Testing (DAST), Static Application
Security Testing (SAST), and Interactive Application Security
Testing (IAST). However, without a culture aligned with
DevSecOps, reported vulnerabilities from DAST might go
unaddressed due to business priorities overshadowing security
concerns. Similarly, vulnerabilities identified through SAST
and IAST may linger unpatched, accumulating in the queue of
vulnerabilities.
Invinsense DevSecOps empowers the
development of a culture that encompasses developers and
processes, prioritizing the patching of application and
infrastructure vulnerabilities. This approachseamlessly
integrates with the development of business logic, ensuring
timely vulnerability patches and averting potential delays.
Invinsense cloud security posture management gives you the complete visibility of your cloud environment. It supports multi-cloud security audits and helps you in maintaining security and compliance of your cloud environment.Using the APIs exposed by various cloud providers, Invinsense CSPM gathers data across your multi-cloud and hybrid environment and highlights risk areas. It presents a single view of the cloud attack surface.

Every organization has various computer infrastructure like VMs, monolithic servers, hosts, containers, Kubernetes, and serverless architecture for its cloud-native applications.Security of each of these computer infrastructures needs different approaches and tools.Invinsense cloud workload protection covers all of them to provide secure deployments covering the entire application lifecycle.
Invinsense Defense in Depth is a five layered single agent security tool for protecting your cloud applications. It provides layered security to your applications.
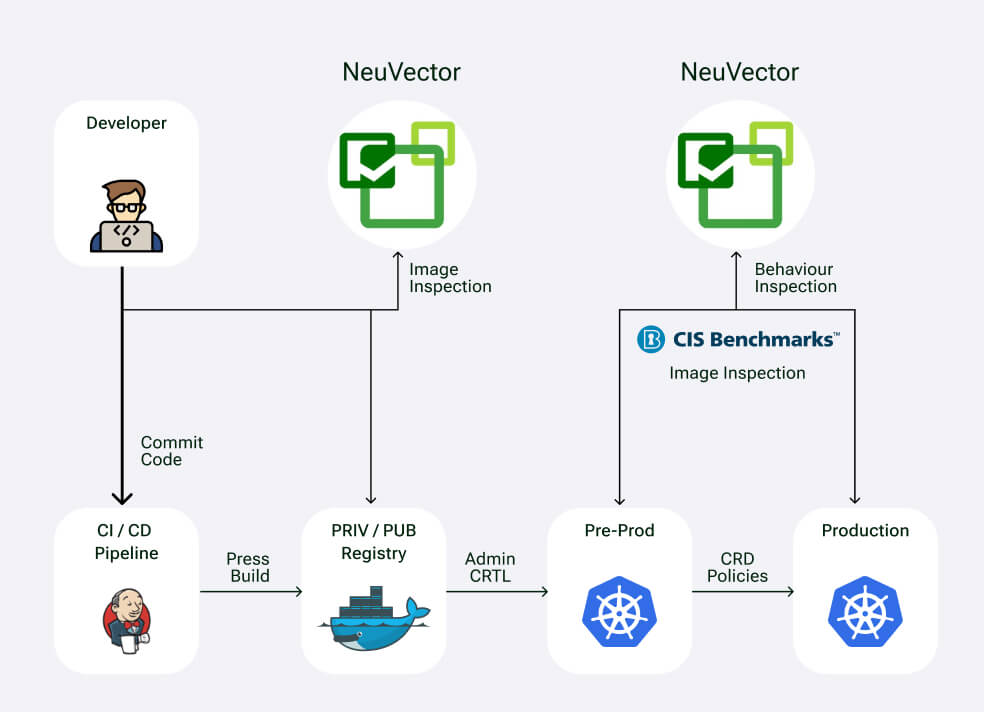
Enterprises deploying containers need to ensure they meet the
highest level of security for containers and Kubernetes.
Invinsense
uses NeuVector for container and Kubernetes security.
NeuVector is a zero-trust, full-lifecycle container security
platform designed to safeguard cloud-native applications from
build to deployment. It offers comprehensive features such as
vulnerability scans, image assurance, runtime security, and
network segmentation.






Copyright © 2024 Infopercept Consulting Pvt. Ltd.. All rights reserved. Privacy Policy / Terms of Use / Cookie preferences
Our website uses cookies to give you the most optimal experience online by: measuring our audience, understanding how our webpages are viewed and improving consequently the way our website works, providing you with relevant and personalized marketing content.You have full control over what you want to activate. You can accept the cookies by clicking on the Accept all cookies button or customize your choices by selecting the cookies you want to activate. You can also decline all non-necessary cookies by clicking on the Decline all cookies button. Please find more information on our use of cookies and how to withdraw at any time your consent on our privacy policy.
Our website uses cookies. You have full control over what you want to activate. You can accept the cookies by clicking on the Accept all cookies button or customize your choices by selecting the cookies you want to activate. You can also decline all non-necessary cookies by clicking on the Decline all cookies button.
These are essential for the user navigation and allow to give access to certain functionalities such as secured zones accesses. Without these cookies, it won't be possible to provide the service.
These are essential for the user navigation and allow to give access to certain functionalities such as secured zones accesses. Without these cookies, it won't be possible to provide the service.
These cookies collect information about your use of the website, such as webpages visited and any error messages; they do not collect personally identifiable information, and the information collected is aggregated such that it is anonymous. Performance cookies are used to improve how a website works.
These cookies are used to deliver advertisements more relevant for you, limit the number of times you see an advertisement; help measure the effectiveness of the advertising campaign; and understand people's behavior after they view an advertisement.
These cookies are used to deliver advertisements more relevant for you, limit the number of times you see an advertisement; help measure the effectiveness of the advertising campaign; and understand people's behavior after they view an advertisement.