Invinsense OT Security Solutions and Services : Safeguarding Operational Technology

This 2-hour workshop with your team will help us discover the current stage of security of your organization, awareness of OT infrastructure, establishing the need of OT security in your set up, a case study discussion of a real-life OT attack, and real time simulation.
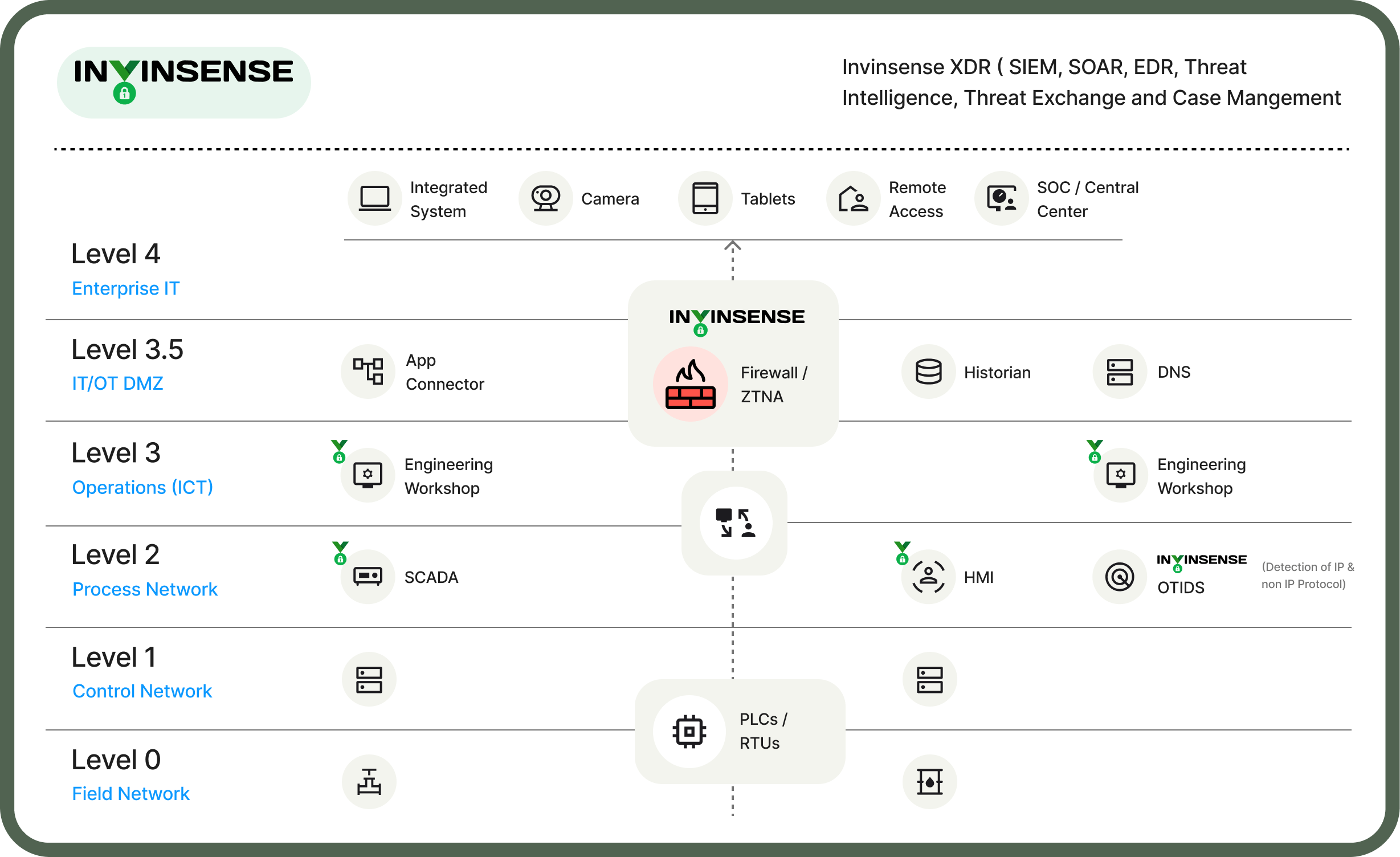
Invinsense does an overall assessment of your OT network including risk assessment followed by technical, physical, and security posture assessments. It leverages CEA guidelines, NCIIPC, IEC‐62443, NIST, Cert-In, and other industry standards as a baseline and existing ENEL frameworks as a starting point for assessment. The assessment is done by reviewing ICS policies and procedures, documentation, network architecture, patching mechanism, and data transfer mechanism followed by vulnerability assessment and security configuration review of OT assets like HMI, engineering workstations, servers, etc.
Infopercept helps you with cybersecurity transformation in four steps:
Infopercept is a part of OT acceleration program by National Center of Excellence (N-CoE) an initiative by Data Security Council of India (DSCI). OT Acceleration Program is Aimed at Productization of OT Security Research and Associations. It brings together researchers, associations, and OT-end customers on the same platform.
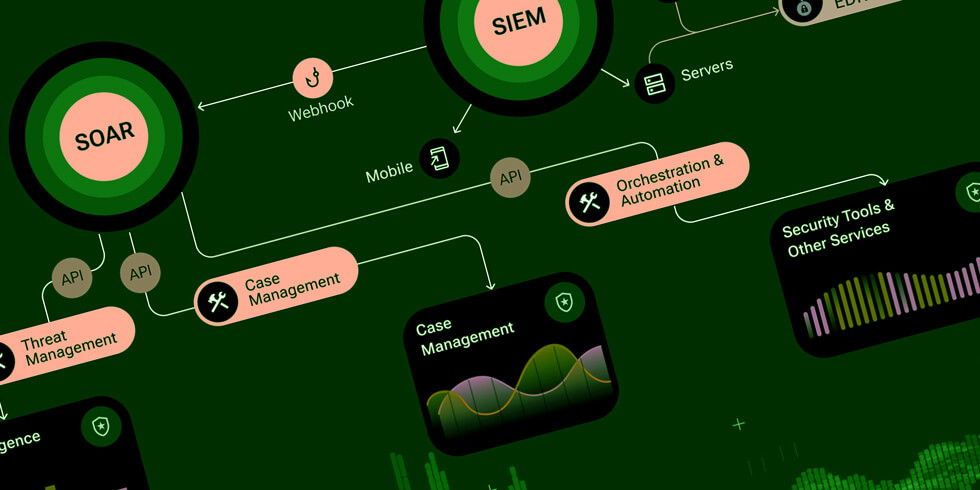
Invinsense provides a range of security solutions that combine offensive and defensive security strategies. Invinsense OT security solutions provides security defender’s brain and an attacker’s mind. It also combines an attacker’s action.
Invinsense OT SIEM (Security Information and Event Management) provides comprehensive monitoring, correlation, and analysis of security events within OT environments. It collects and analyses log data from various OT devices, systems, and applications to security teams in order to detect and respond to cybersecurity incidents in critical industrial infrastructure.
Invinsense OT SOAR (Security Orchestration, Automation, and Response) utilizes predefined incident response playbooks tailored for your OT systems. These playbooks outline the step-by-step actions to be taken in response to specific security incidents, ensuring a consistent and efficient response that ultimately increases the operational efficiency of the OT environments.
Invinsense OT endpoint protection is designed to detect and block known and unknown malware targeting your OT systems. It does the behavioral analysis of OT endpoints and detects anomalous or suspicious activities that could indicate a cyber-attack. It also ensures that the OT endpoints are kept up-to-date with the latest software patches and security updates to address known vulnerabilities.
Invinsense OT IDS is a signature-based detection system that compares network traffic against a vast database of known attack patterns and signatures to identify common threats. It decodes and understands the intricacies of industrial protocols to identify any signs of malicious commands or unauthorized access. When suspicious activity is detected, Invinsense OT IDS generates alerts and notifications to security administrators, enabling them to respond quickly to potential security incidents.
Invinsense OT firewall is designed to protect your OT systems and assets from cyber threats. It is specifically tailored to secure industrial control systems (ICS) and other OT devices used in your organization. It offers deep packet inspection (DPI), protocol filtering for OT protocols like Modbus, DNP3, OPC-UA, and IEC 60870-5-104, etc., network segmentation, application filtering, and anomaly detection.
Invinsense OT ZTNA offers robust OT security with identity-centric least privilege access. That means it ensures that users and devices are authenticated and authorized before accessing any resources. It provides just a minimum level of access for users to perform their specific tasks, reducing the risk of unauthorized access or privilege escalation.
Invinsense OT Deception deploys decoys within your OT environment to mislead and detect potential attackers. These decoys mimic legitimate devices and applications, making them appear as enticing targets to potential adversaries. This strategy provides valuable threat intelligence, such as the attacker's techniques, tools, and intentions, which can be used to enhance the organization's overall cybersecurity posture.
Patching, in conjunction with software updates and system reconfiguration, forms a vital component of IT system lifecycle management.Invinsense Patch Management streamlines patch deployment, generates comprehensive reports on patched systems, identifies systems requiring updates, and highlights noncompliant systems.
Invinsense OT attack surface monitoring constantly monitors the attack surface and take actions in case of any threats. Invinsense OT Vulnerability Management identifies, prioritizes, and mitigates vulnerabilities in your OT systems to reduce the risk of cyberattacks and ensure the security and reliability of critical industrial infrastructure.
Invinsense GSOS is a consolidated compliance platform which helps organizations to achieve OT security compliances like CEA guidelines, NCIIPC, IEC‐62443, NIST and Cert-In
Invinsense offers a dedicated OT SOC that integrates and manages all the above cybersecurity technologies and operations. It helps you develop your cybersecurity strategy from scratch and implement it smoothly.The SOC team monitors your OT networks 24/7 for security events and anomalies. It detects security incidents in real time, investigates the impact, and initiates appropriate response actions to contain and mitigate the threats.Once the incident is contained the SOC team re-evaluates the overall security, helps in the recovery of affected assets, and uses the intelligence from the incident to strengthen the security posture of the organization.






Copyright © 2024 Infopercept Consulting Pvt. Ltd.. All rights reserved. Privacy Policy / Terms of Use / Cookie preferences
Our website uses cookies to give you the most optimal experience online by: measuring our audience, understanding how our webpages are viewed and improving consequently the way our website works, providing you with relevant and personalized marketing content.You have full control over what you want to activate. You can accept the cookies by clicking on the Accept all cookies button or customize your choices by selecting the cookies you want to activate. You can also decline all non-necessary cookies by clicking on the Decline all cookies button. Please find more information on our use of cookies and how to withdraw at any time your consent on our privacy policy.
Our website uses cookies. You have full control over what you want to activate. You can accept the cookies by clicking on the Accept all cookies button or customize your choices by selecting the cookies you want to activate. You can also decline all non-necessary cookies by clicking on the Decline all cookies button.
These are essential for the user navigation and allow to give access to certain functionalities such as secured zones accesses. Without these cookies, it won't be possible to provide the service.
These are essential for the user navigation and allow to give access to certain functionalities such as secured zones accesses. Without these cookies, it won't be possible to provide the service.
These cookies collect information about your use of the website, such as webpages visited and any error messages; they do not collect personally identifiable information, and the information collected is aggregated such that it is anonymous. Performance cookies are used to improve how a website works.
These cookies are used to deliver advertisements more relevant for you, limit the number of times you see an advertisement; help measure the effectiveness of the advertising campaign; and understand people's behavior after they view an advertisement.
These cookies are used to deliver advertisements more relevant for you, limit the number of times you see an advertisement; help measure the effectiveness of the advertising campaign; and understand people's behavior after they view an advertisement.