Some of the leading challenges of security operations experienced by today's organizations include; the cybersecurity skill gap, high costs, and the complexity of building a security operations team in-house and the absence of reliable 24x7 security monitoring.
Business Loss Data Predicition
Data from research done by experts
Global cybercrime damage is predicted to hit $10.5 trillion annually by 2025.

Ransomware damage costs are predicted to grow more than 57X from 2015 to 2021.

Cybersecurity spending will exceed $1 trillion from 2017 to 2021.

Infopercept's Security Operations Services
Infopercept with its team of experienced Cyber Security Experts will be working round the clock to reduce business risks, administrative burden and costs, flexible compliance reporting, and detection of cyberthreats.
With Infopercept's uninterrupted security operations, continuous monitoring takes place on the lookout for new threats that may arise in the IT Landscape. Our effective Security Operations Center (SOC) provides you with peace of mind in terms of your organizational security integrity, enabling you to better focus on the business aspects that matter most to you allowing for better returns on your investment.
We at Infopercept orchestrate multiple roles, processes and technology seamlessly, that is needed to enable efficient incident detection, analysis, and response. Comprising a set of processes, technologies, and a team of trusted security analysts and R&D specialists, each SOC provides complete visibility of both an enterprise's IT and its security system.
Infopercept's very own cybersecurity personnel within its independent Security Operations Centre (SOC) consists of highly trained analysts who work on defending and improving your organization's defenses around the clock. The Blue team will detect and neutralize the more sophisticated attacks and closely monitor current and emerging threats to preemptively defend your organization.
Infopercept's Security Operations Center Roles
The roles and the responsibilities of its members as follows:
SOC Director
The leader of the group who is able to step into any role while also overseeing the overall security systems and procedures.
L1 SOC Analyst
The analysts compile and analyze the data, either from a period of time (the previous quarter, for example) or after a breach.
SOC Investigator
If a breach occurs, the investigator finds out what happened and why, working closely with the responder (often one person performs both 'investigator' and "responder" roles).
SOC Responder
There are a number of tasks that come with responding to a security breach. An individual familiar with these requirements is indispensable during a crisis.
SOC Auditor
Infopercept being proactive is ready to meet the compliance mandates of the current and future legislations. This role keeps up with these requirements and ensures your organization meets them.

To make Infopercept's Security Operations Center effective, we have defined and documented processes so that the execution can be ensured in accordance with the documented plan. These processes ensure the synchronization and timely execution of different events and activities that are performed by the SOC with the following services.
- Security Devices Monitoring
- Managed Audit/Assessment Services
- Real time Monitoring, analysis and
detection of Security threats - Threat Management
- Forensic Services
- Security Incident Management Service
- Threat Intelligence Services
- Vulnerability Scanning
- SIEM, SOAR, EDR, Deception, MTD Tools
Monitoring and Management
OODA Strategy
In order for the processes to be implemented effectively, Infopercept SOC utilizes next generation technologies to proactively contain unforeseen vulnerabilities. Infopercept SOC is able to provide Superior threat intelligence with advanced analytics; whereby converting data into knowledge in order to see the entire security posture of your organization, rather than looking at it as isolated events. This is done using Security Data Lakes deploying the OODA Strategy.
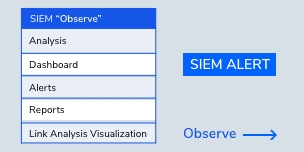
OBSERVE
with SIEM
By making more observations of your network and its operations, Infopercept will be able to successfully defend and respond to incidents.
Using SIEM, Infopercept identifies abnormal behaviors that might be requiring investigation.
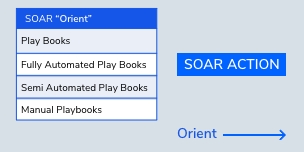
ORIENT
with SOAR
By getting inside the mindset of cybercriminals, Infopercept is able orient defense strategies against the latest attack tools & tactics.
With the effective use of SOAR, Infopercept enables organizations to evaluate on the incidents taking place across your IT Landscape. By doing so Infopercept is able to focus in Realtime Context.
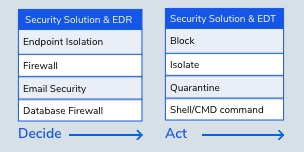
DECIDE & ACT
with EDR
Based on the observations and the Orientation, Infopercept will use the EDR to Decide and Act so that threats could be averted using Endpoint Response and Detection, threats so that there's minimal damage to your organization with faster recovery.

OBSERVE
with SIEM
By making more observations of your network and its operations, Infopercept will be able to successfully defend and respond to incidents.
Using SIEM, Infopercept identifies abnormal behaviors that might be requiring investigation.

ORIENT
with SOAR
By getting inside the mindset of cybercriminals, Infopercept is able orient defense strategies against the latest attack tools & tactics.
With the effective use of SOAR, Infopercept enables organizations to evaluate on the incidents taking place across your IT Landscape. By doing so Infopercept is able to focus in Realtime Context.

DECIDE & ACT
with EDR
Based on the observations and the Orientation, Infopercept will use the EDR to Decide and Act so that threats could be averted using Endpoint Response and Detection, threats so that there's minimal damage to your organization with faster recovery.
Why Choose Infopercept SOC?
A good SOC plan effectively edges out your competition and brings in better comparative revenue.
Security Expertise
Security Operation Center that operates with certified security experts 24/7.
Immediate Response
Infopercept's team of security experts possess the skills to help organizations promptly identify threats, perform forensics analysis, apply threat intelligence and detect high-priority incidents that require immediate response.
SIEM Management
SIEM configuration, custom rule implementation and platform management including health and availability, software patching and backup.


Security Data Lakes
Infopercept's Security Data Lake is a highly scalable, fault tolerant, open data platform that ingests massive amounts of data and supports reliable and economical long-term data retention.
Business and compliance reporting
Events that indicate a deviation from your defined baseline of regulatory and business policy compliance requirements
Enables Organizations to Grow not Hire
Recruiting cybersecurity experts is a challenge and screening them can take some time. Maintaining the Cybersecurity qualifications of these experts requires time and a significant budget to be invested. With Infopercept's SOC, the above mentioned challenges are eliminated.
Increase Revenue
Implementing an internal SOC involves a considerable investment. Infopercept's SOC allows organizations to extend your offerings whilst allowing your internal resources to focus on winning new business and developing client relationships.

 Casestudy
Casestudy
 Whitepaper
Whitepaper


