Subdomain Takeover AWS S3 bucket
On November 7, 2023
Introduction
A subdomain is a domain that is part of a larger domain. In a domain name, the subdomain is the part that precedes the main domain and is separated by a dot. For example, in the domain name “subdomain.example.com,” “subdomain” is the subdomain, “example” is the main domain, and “.com” is the top-level domain.
Subdomains can be registered and managed separately from the main domain, and they may have their own unique content, server, and security settings. However, subdomains are still part of the same overall domain, and they inherit some of the properties of the main domain, such as the same IP address, security certificate, and domain ownership.
AWS S3 (Amazon Web Services Simple Storage Service)
It is a highly popular cloud storage service that is used by individuals and organizations to store and retrieve data. One of the features of AWS S3 is the ability to host static websites, which can be accessed via a unique endpoint or subdomain. While this feature is useful for hosting static websites, it also presents a security risk called subdomain takeover.
Subdomain takeover
Subdomain takeover occurs when an attacker gains control of a subdomain that is pointing to an AWS S3 bucket that they do not own or control. This can happen when the owner of the S3 bucket deletes it, and the subdomain continues to point to the now non-existent bucket. An attacker can then create a new S3 bucket with the same name and take control of the subdomain
Step to Reproduce
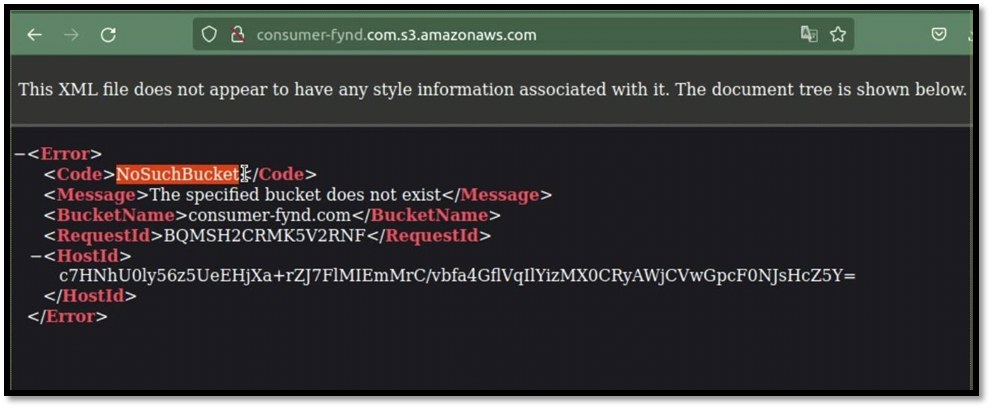
Found Subdomain using subdover tool.
Subdomain CNAME record is not deleted from target.com DNS zone, anyone who registers anotherdomain.com has full control over sub.example.com until the DNS record is present.
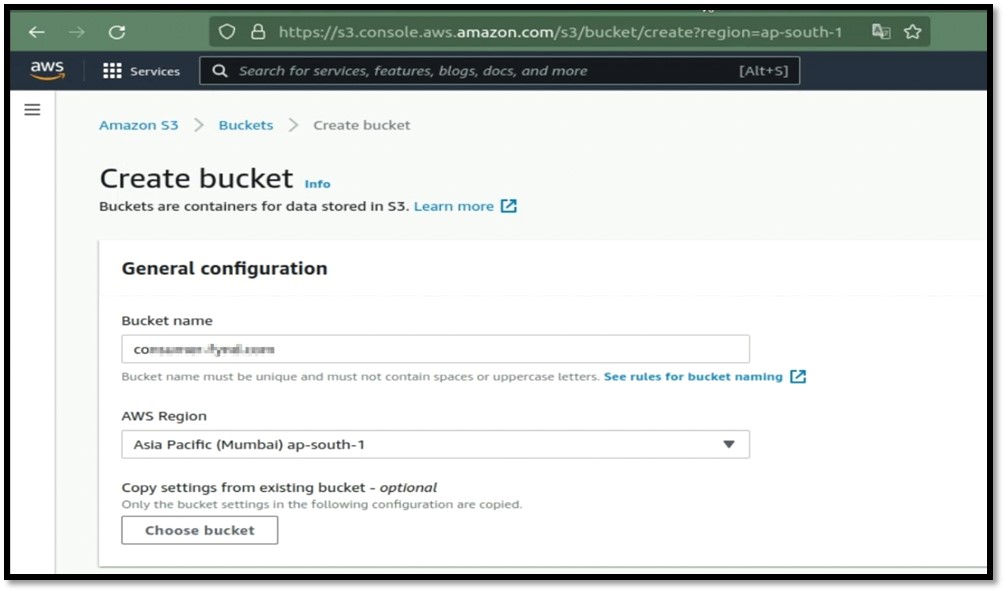
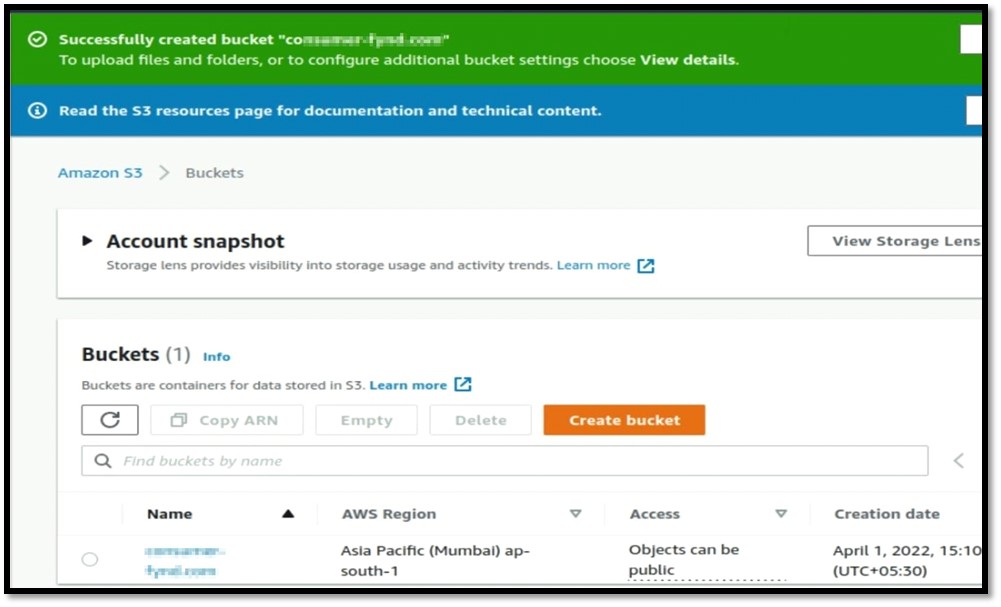
Now go to the AWS to create the s3 bucket by filling bucket name and AWS region.
Now it’s time to upload the index file.
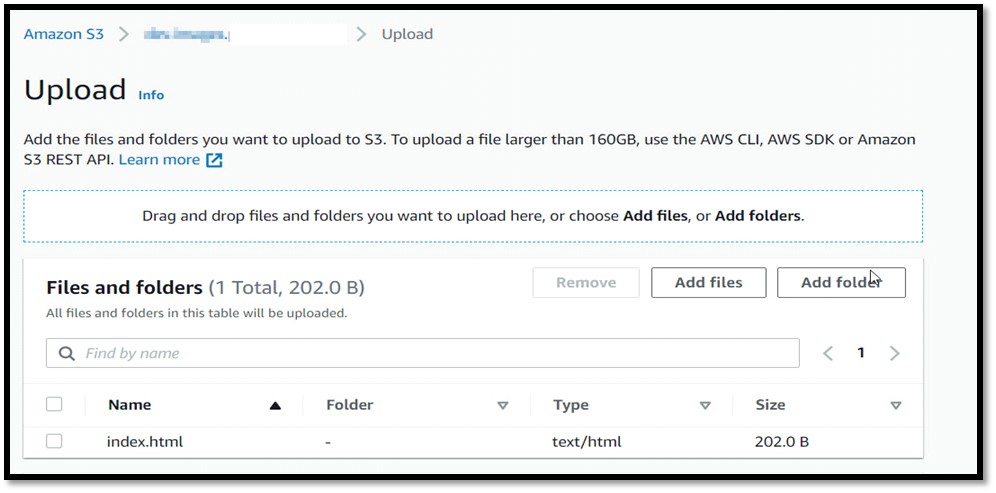
Let’s check the sub domain after uploading the index file.
The consequences of subdomain takeover can be severe, as an attacker can use the subdomain to launch phishing attacks, distribute malware, or conduct other malicious activities. This can damage the reputation of the affected organization and cause financial losses.
Remediation
It is important to monitor subdomains that point to AWS S3 buckets regularly. The following are some of the measures that can be taken to prevent subdomain takeover:
• Remove DNS records pointing to non-existent buckets: DNS records that point to non-existent buckets should be removed as soon as possible to prevent them from being taken over by attackers.
• Implement access controls: Access controls can be implemented to prevent unauthorized access to S3 buckets. This can be achieved by configuring bucket policies, access control lists (ACLs), and using AWS Identity and Access Management (IAM).
• Monitor subdomains: Regularly monitor subdomains to ensure that they are pointing to the correct S3 bucket. This can be achieved by using tools such as Subfinder, Sublist3r, and AWS S3 scanner.
• Implement a Content Delivery Network (CDN): Implementing a CDN can help to prevent subdomain takeover by providing an additional layer of protection. A CDN can cache the content of the S3 bucket and serve it from multiple locations, reducing the risk of a single point of failure.
Conclusion
Subdomain takeover is a serious security risk that can have severe consequences. It is important to take preventive measures to ensure that subdomains pointing to AWS S3 buckets are secure. By regularly monitoring subdomains, removing DNS records pointing to non-existent buckets, implementing access controls, and implementing a CDN; you can reduce the risk of subdomain takeover and ensure the security of your AWS S3 buckets.





